Demo video: Send events to APEX AIOps Incident Management from New Relic ►
This video explains how to set up the New Relic integration in APEX AIOps Incident Management.
*Please note Moogsoft is now part of Dell's IT Operations solution called APEX AIOps, and changed its name to APEX AIOps Incident Management. The UI in this video may differ slightly but the content covered is still relevant.
After watching this video, you will be able to create an integration to ingest New Relic incidents and set up a webhook in New Relic.
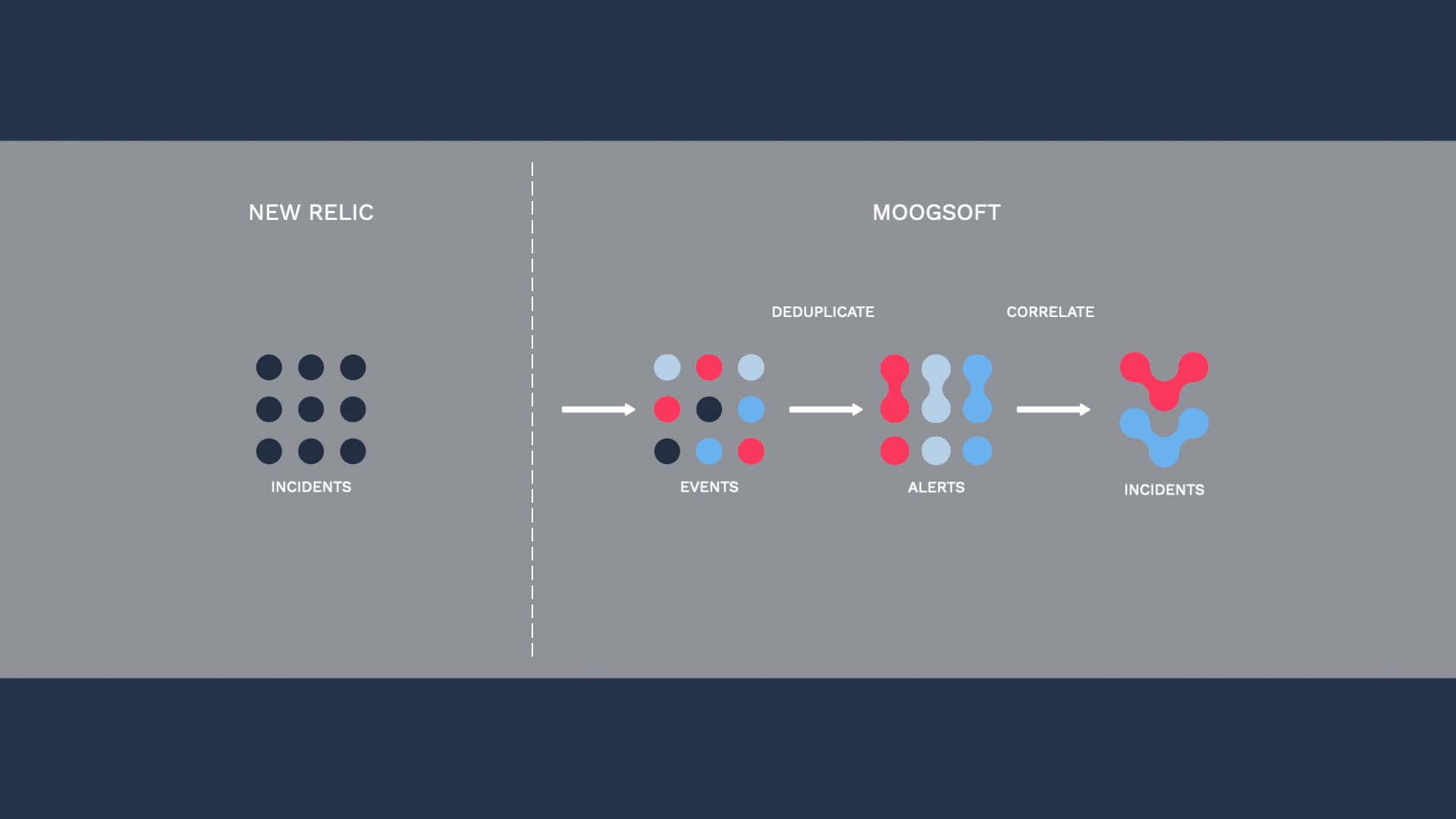
Here’s our scenario. We want to ingest alerts identified by New Relic so we can deduplicate and correlate them in Incident Management.
Here’s the New Relic integration.
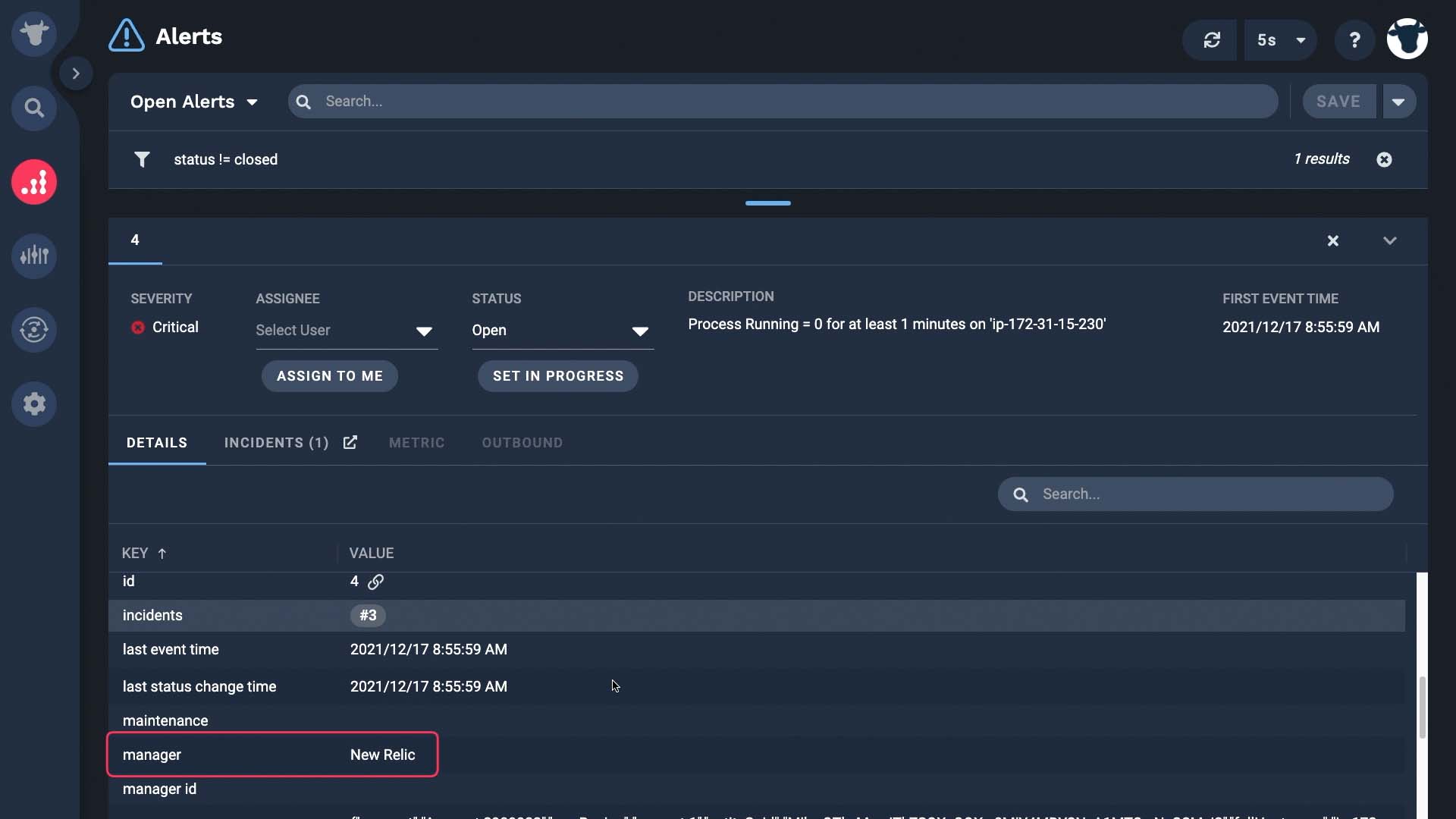
The API is provisioned. We’ll make it active after we finish setting it up.
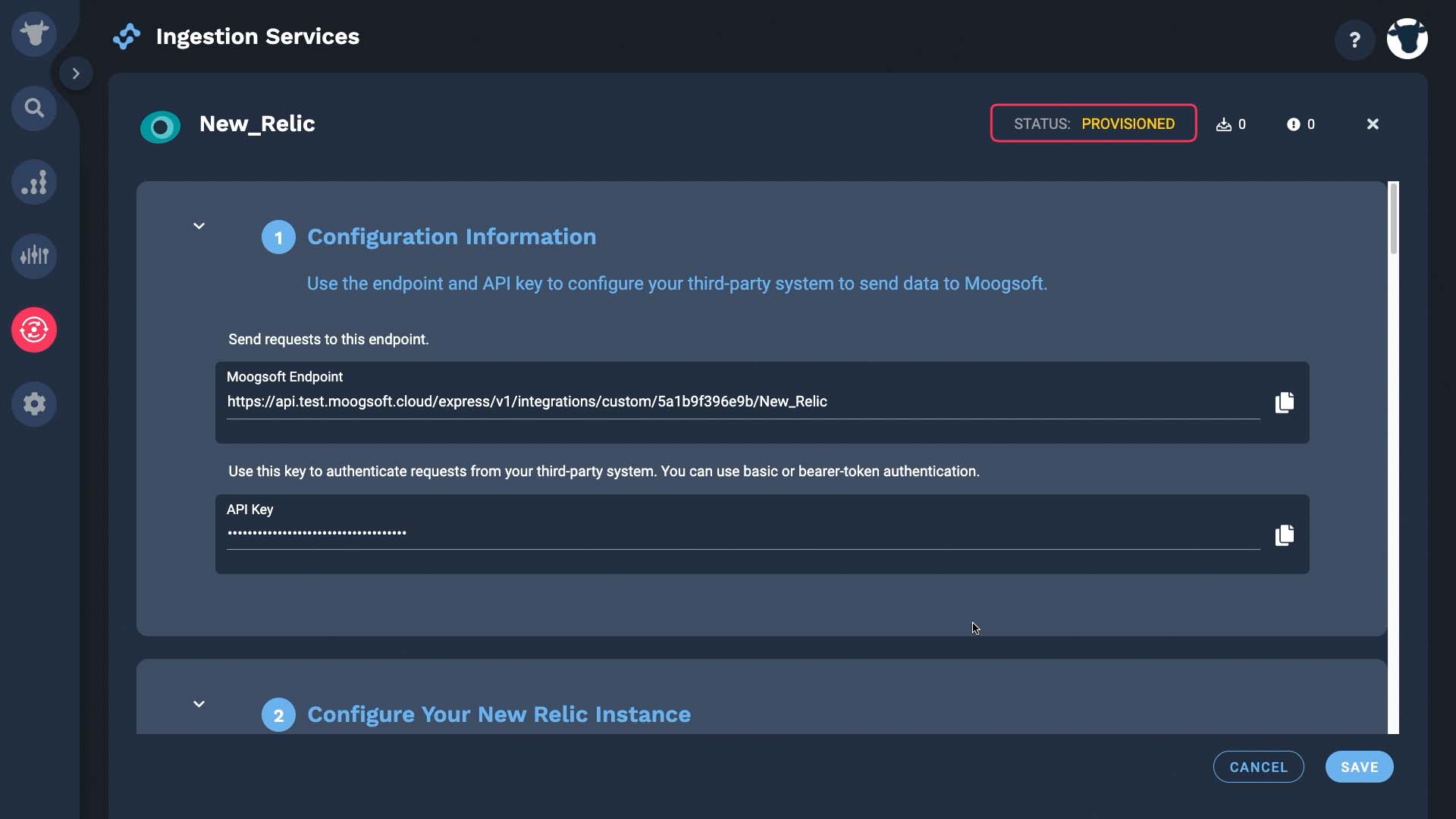
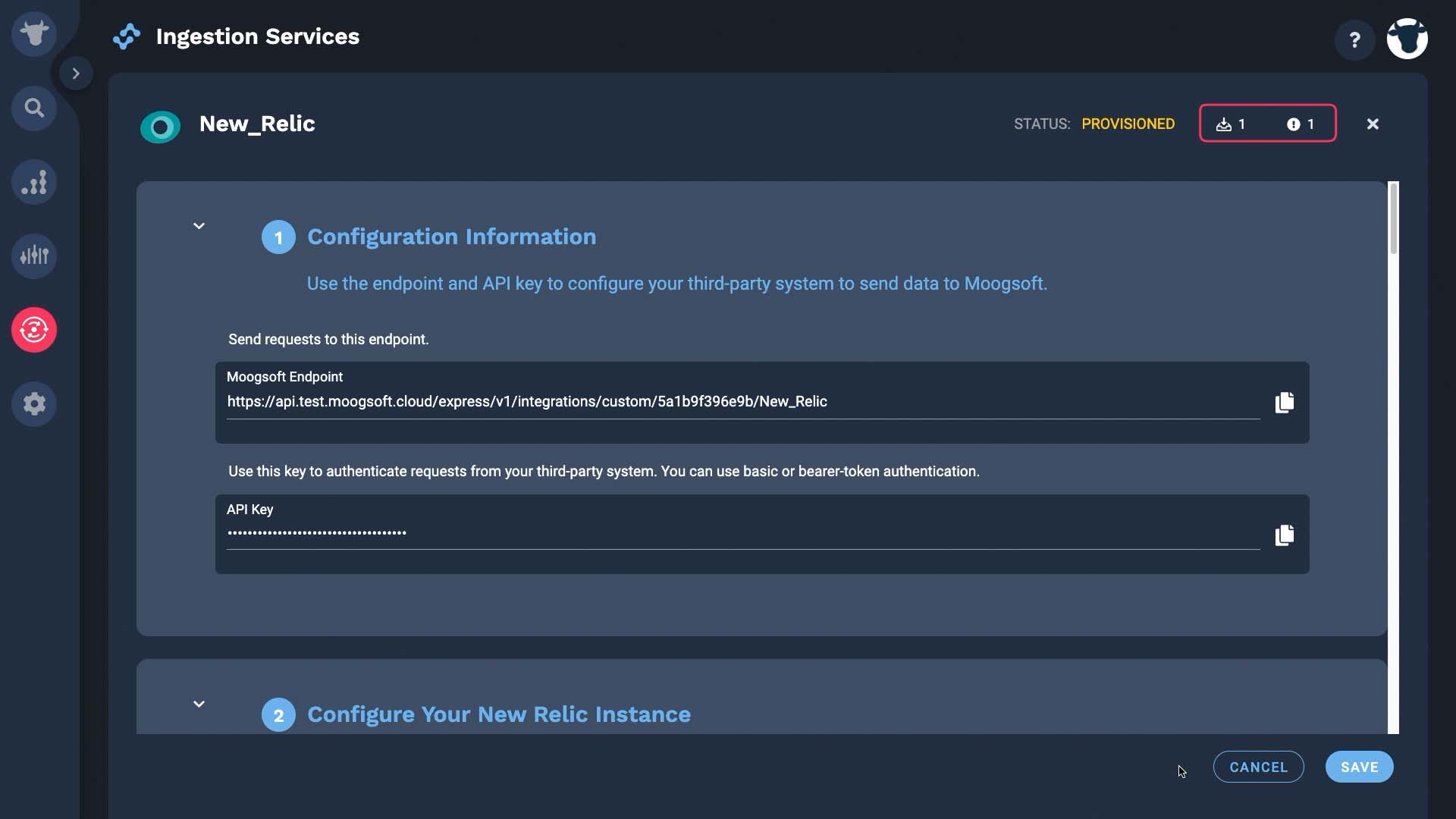
Next we are going to get data from New Relic. Incident Management will cache up to 10 New Relic events until the integration is active. These counters show how many payloads we’ve received - so far, in this case, none.
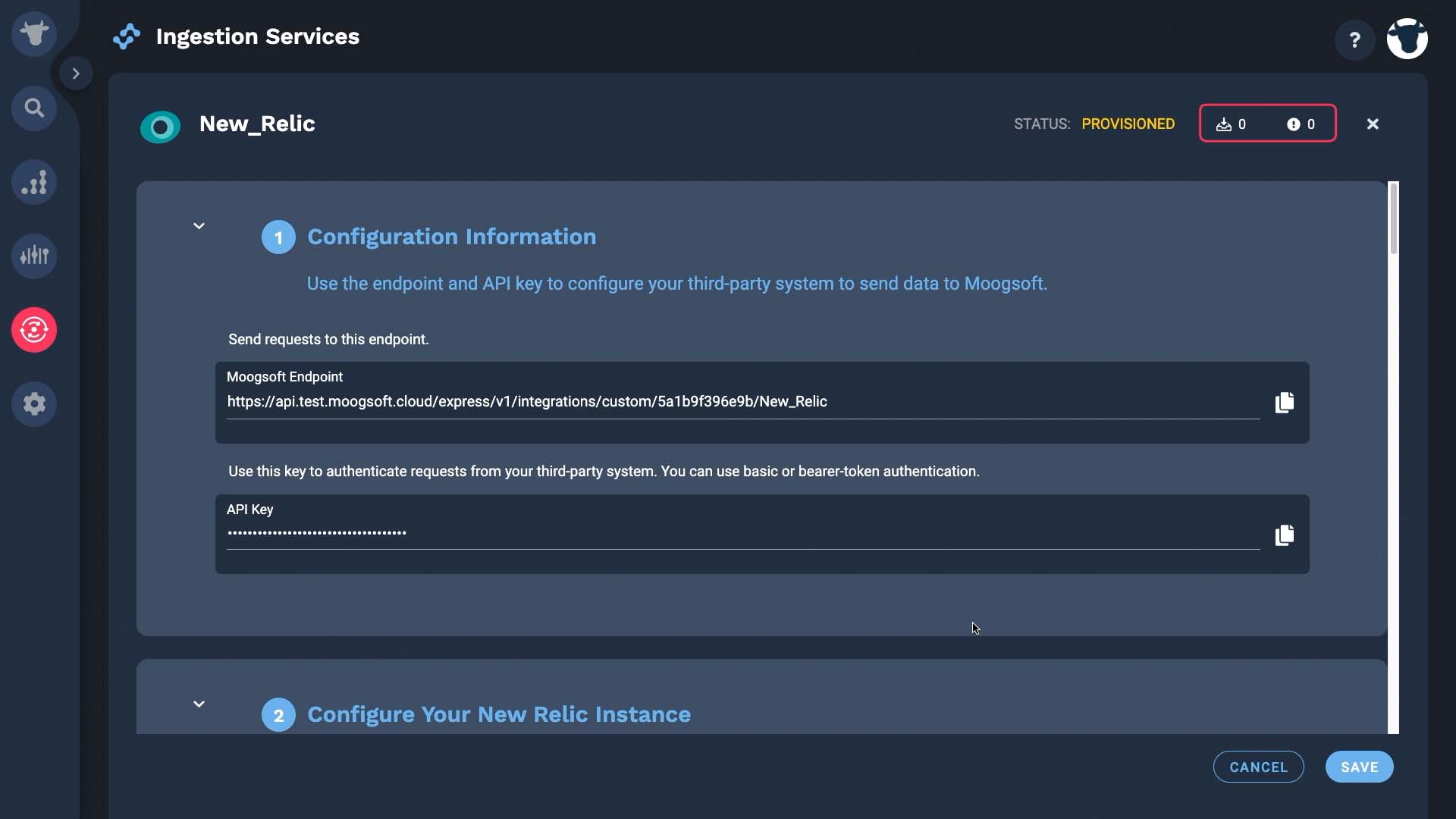
These are what we need.
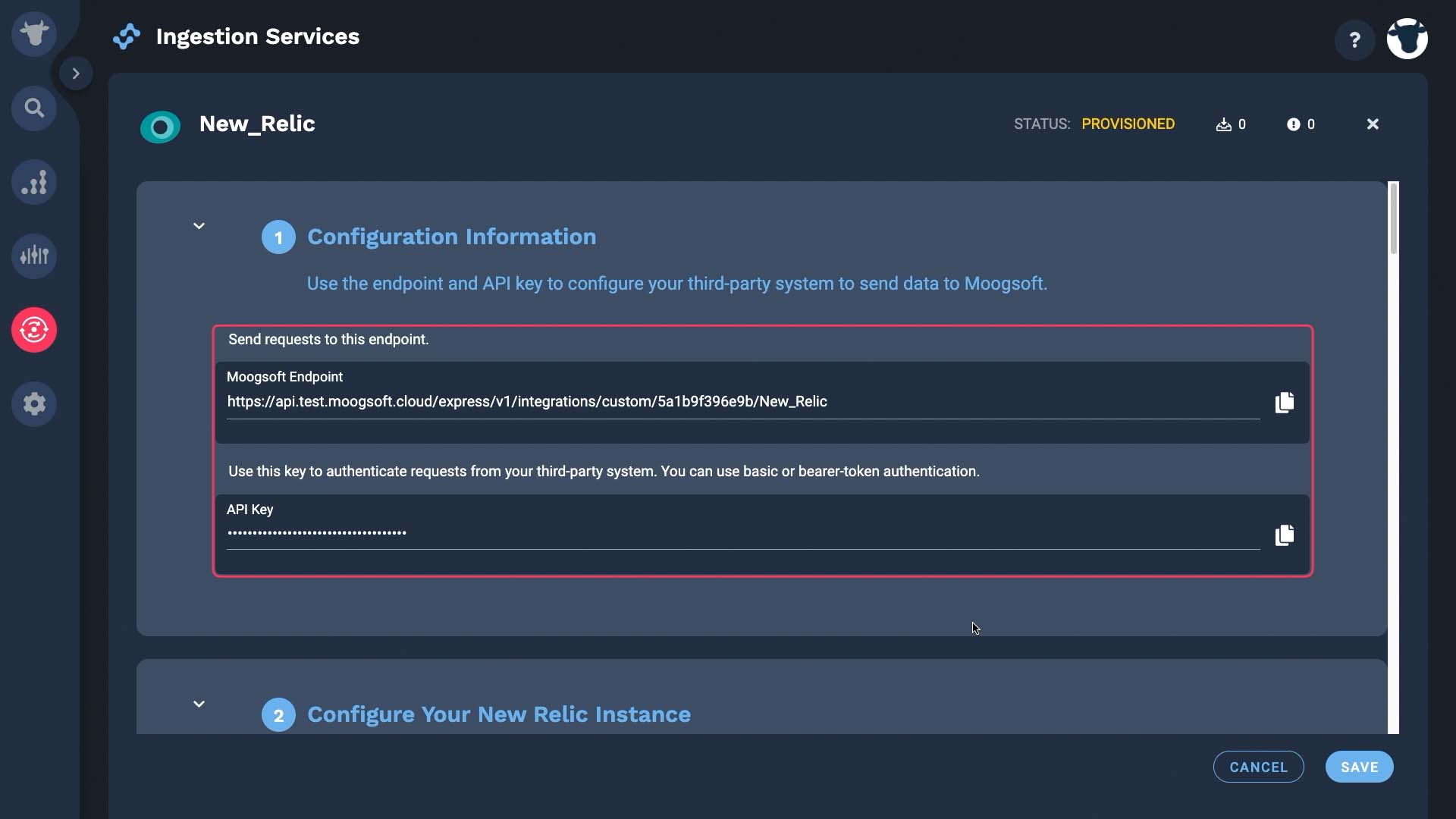
Now going back to New Relic. We’ll start by configuring a notification channel to send issues to Incident Management.
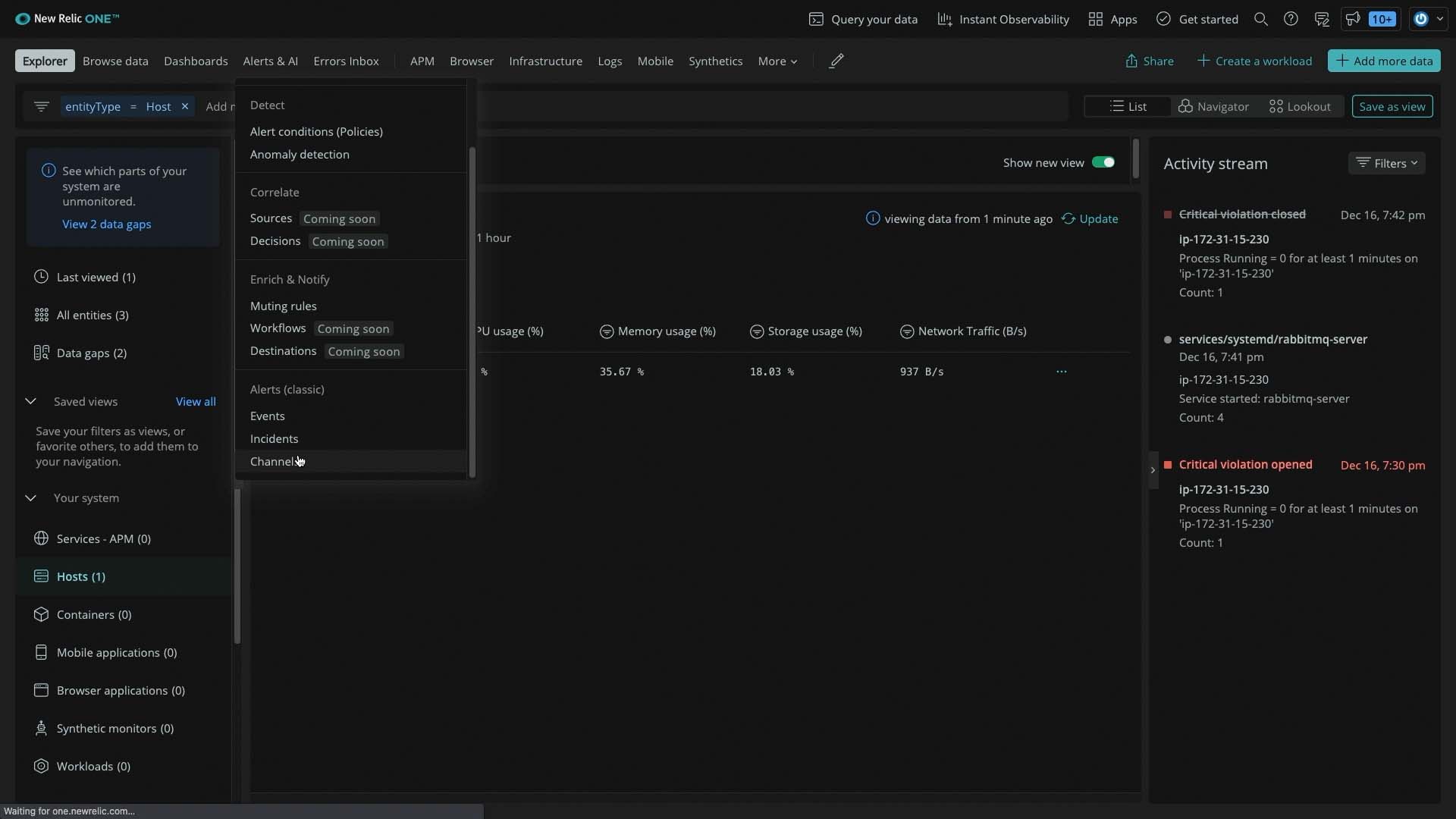
The channel type is webhook.
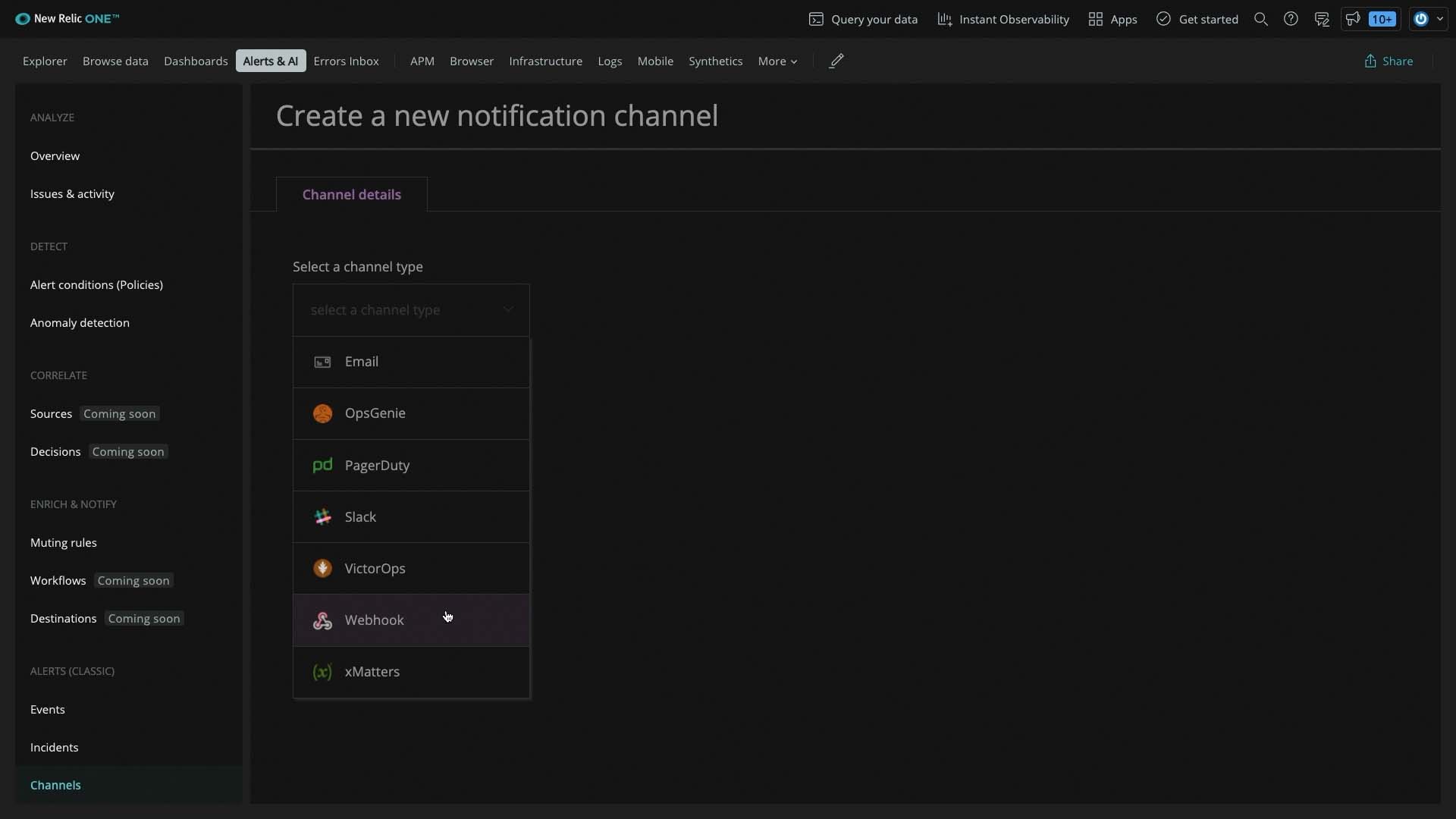
...and this is where you paste the Incident Management Endpoint API URL we grabbed.
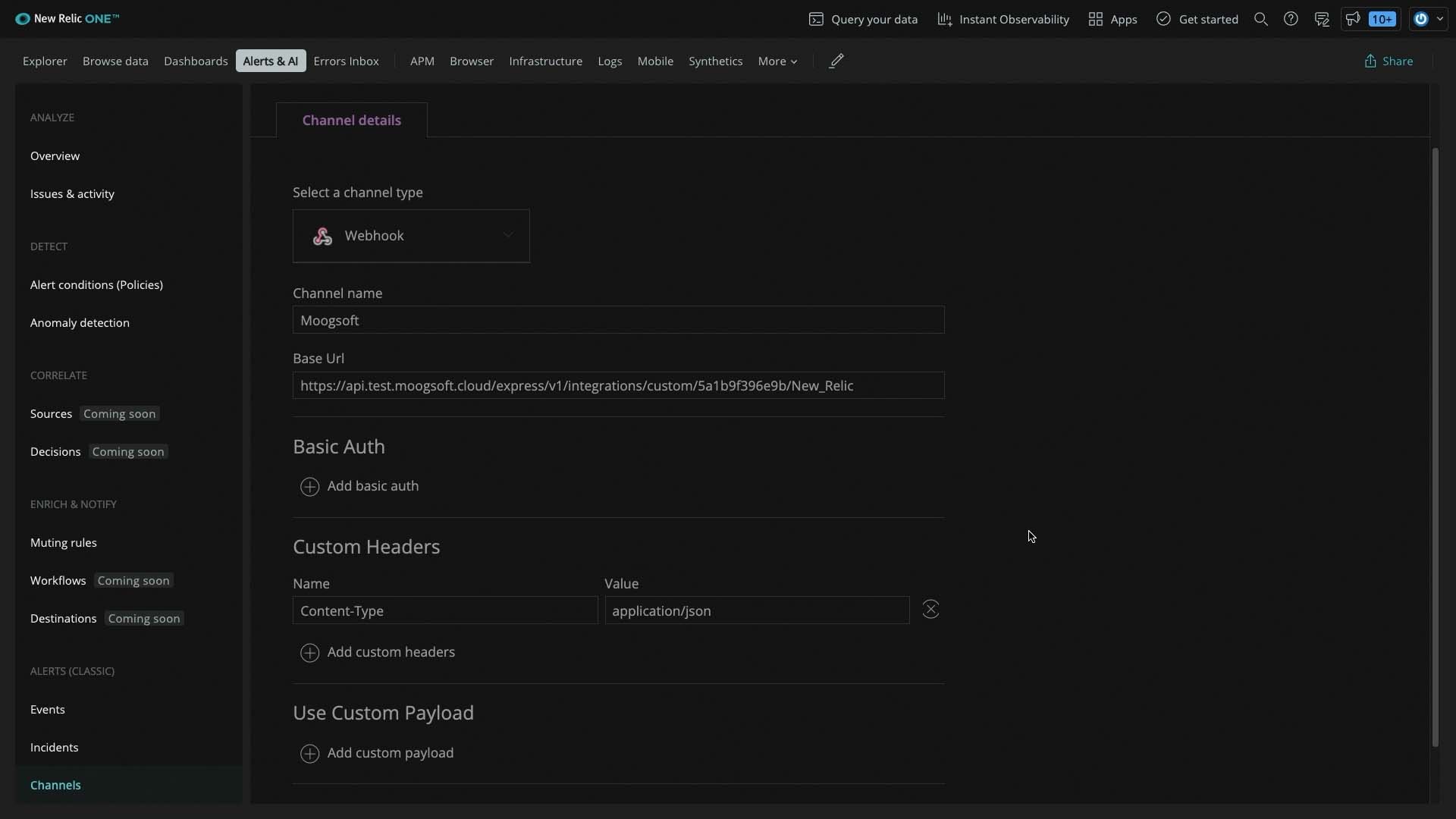
We need some custom request headers for our data payload. The content type is application/json.
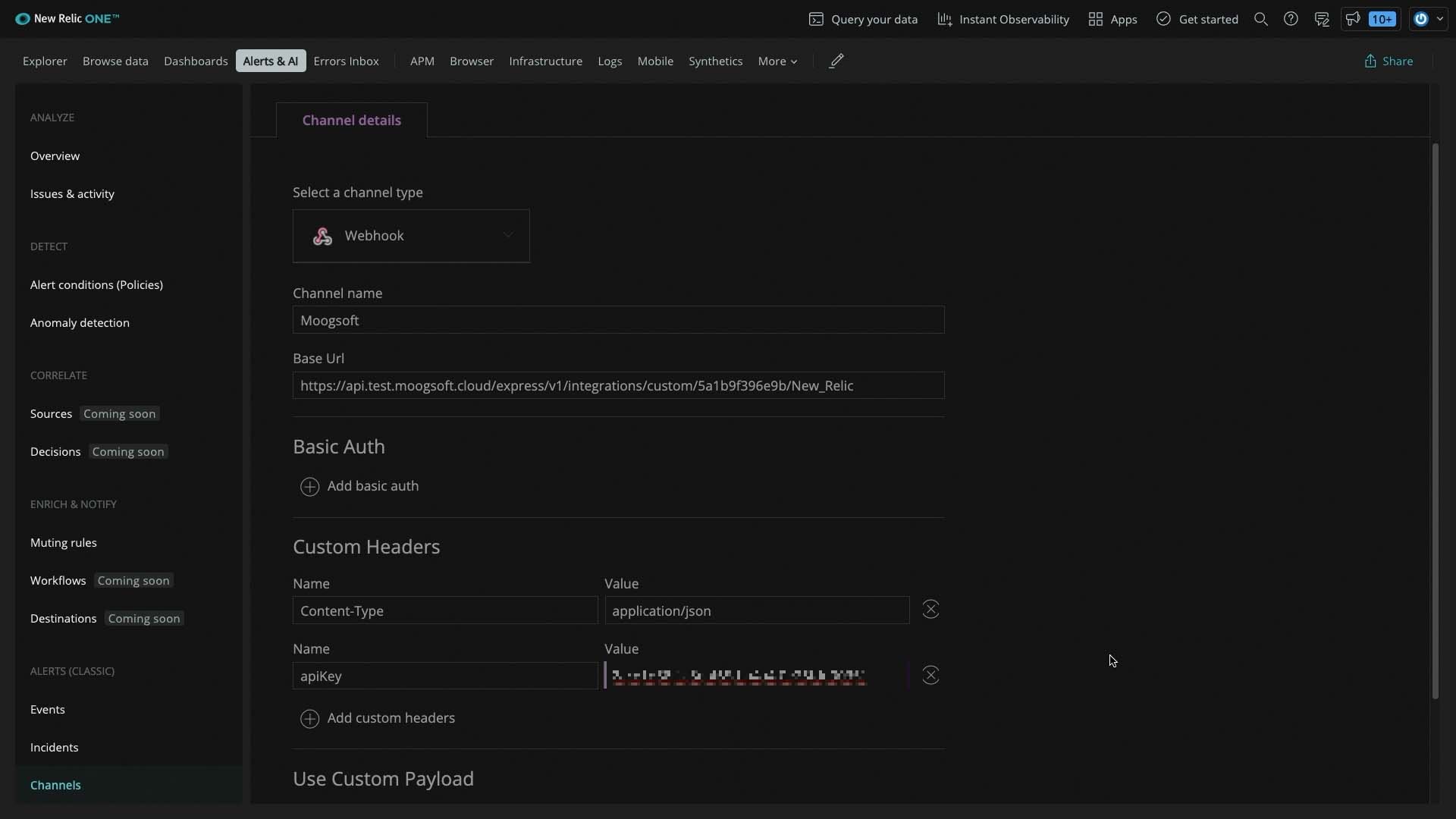
And here is where we enter the apiKey.
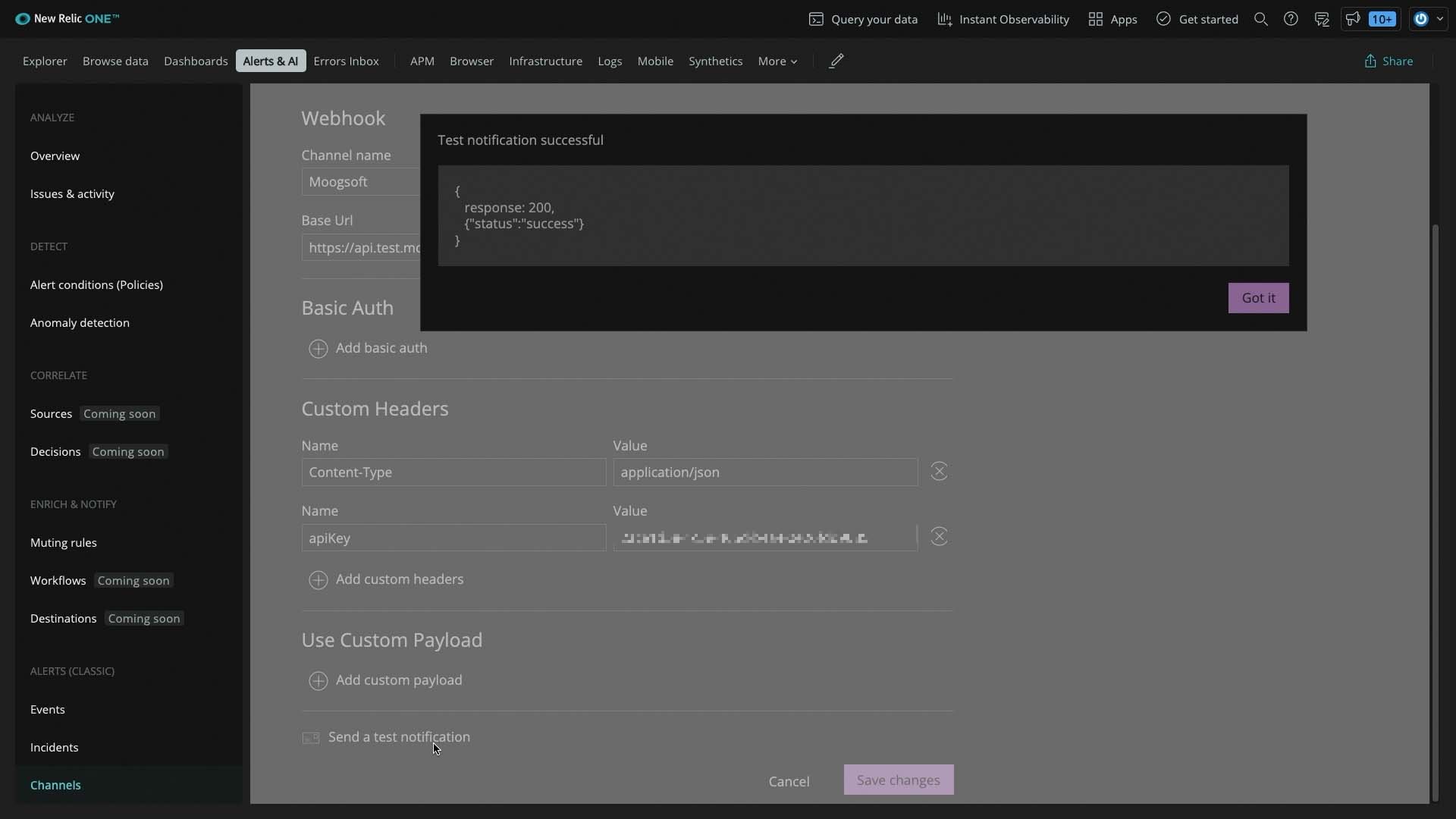
We’ll use the default New Relic output, so we don’t need to set up a custom data payload and test these settings. Good!
Make sure to add this notification to the New Relic policy associated with the alerts you want to send to Incident Management.
The test notification showed up in Incident Management.
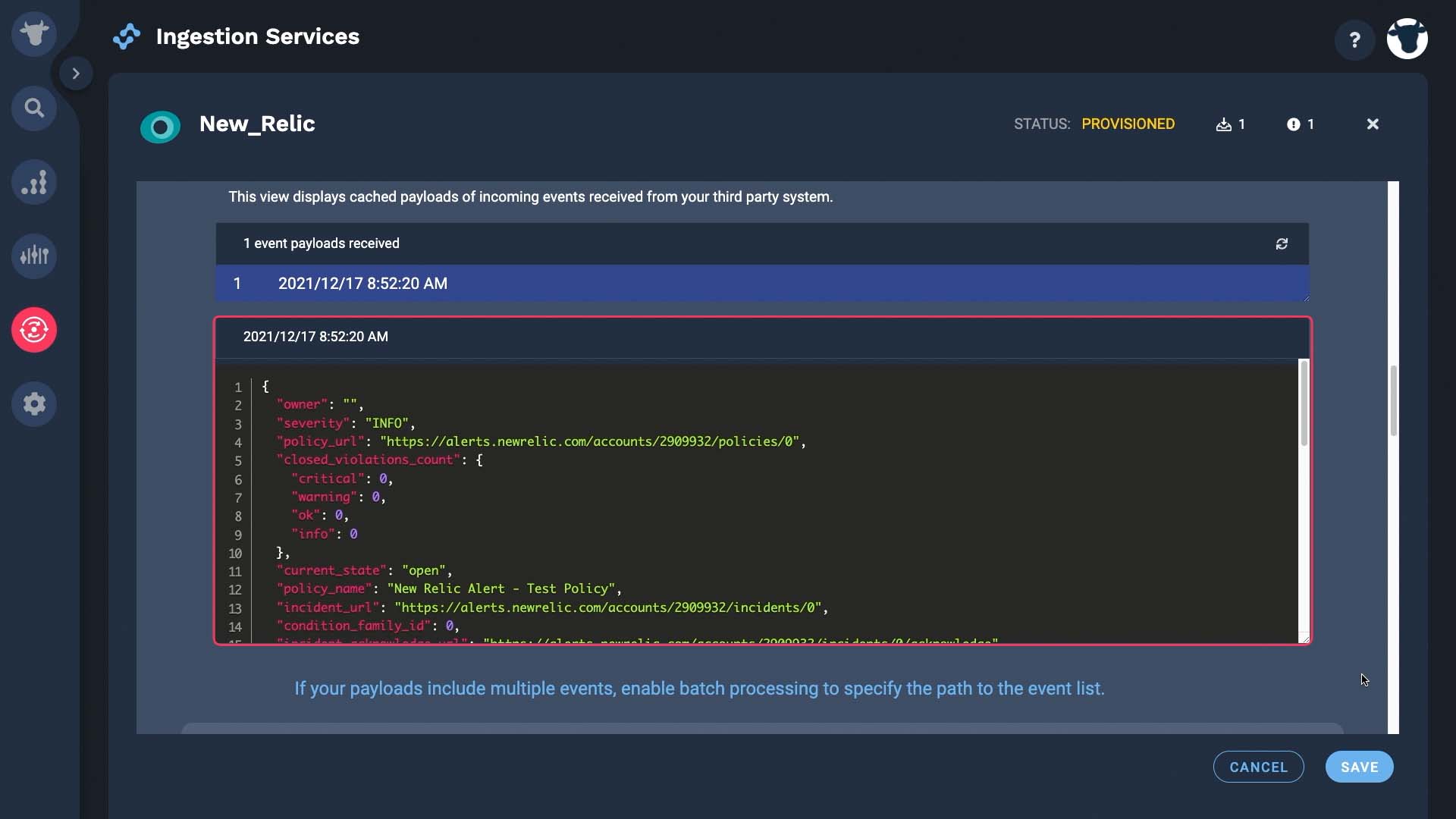
Here's the JSON payload from the test notification.
Field mapping is preconfigured to make it easy for you.
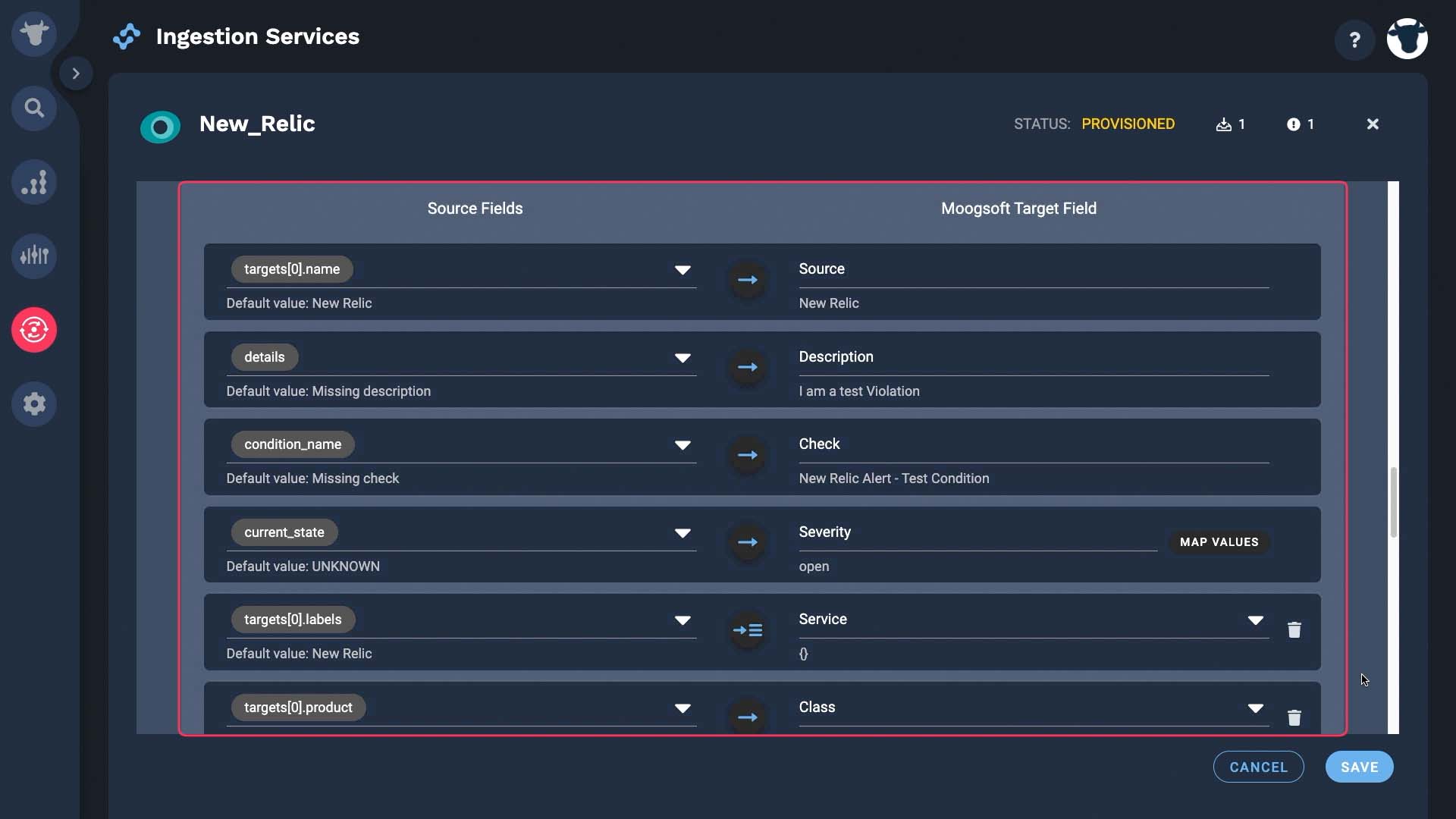
Optionally, at this point, you can also pick the deduplication key. Incident Management uses the dedupe key value to combine events with the same context into a single alert, while updating the alert fields that change over time like description and status. By default Incident Management uses the combination of source, class, service, and check fields. We’ll keep the defaults...
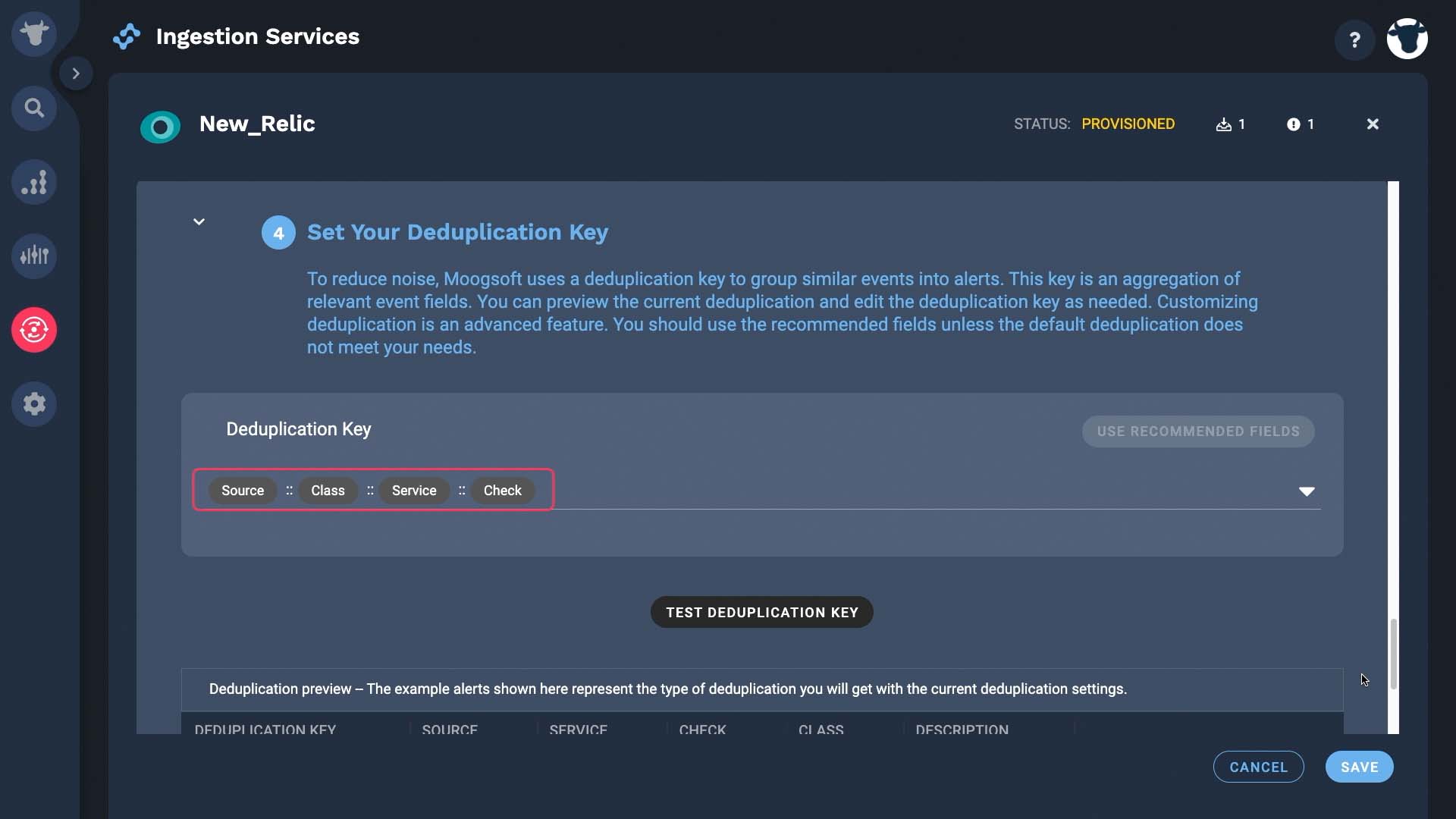
And test the deduplication key. Looks good! Now when another event with the same value for this field comes in, Incident Management will update alert fields like latest event arrival time and severity, as needed.
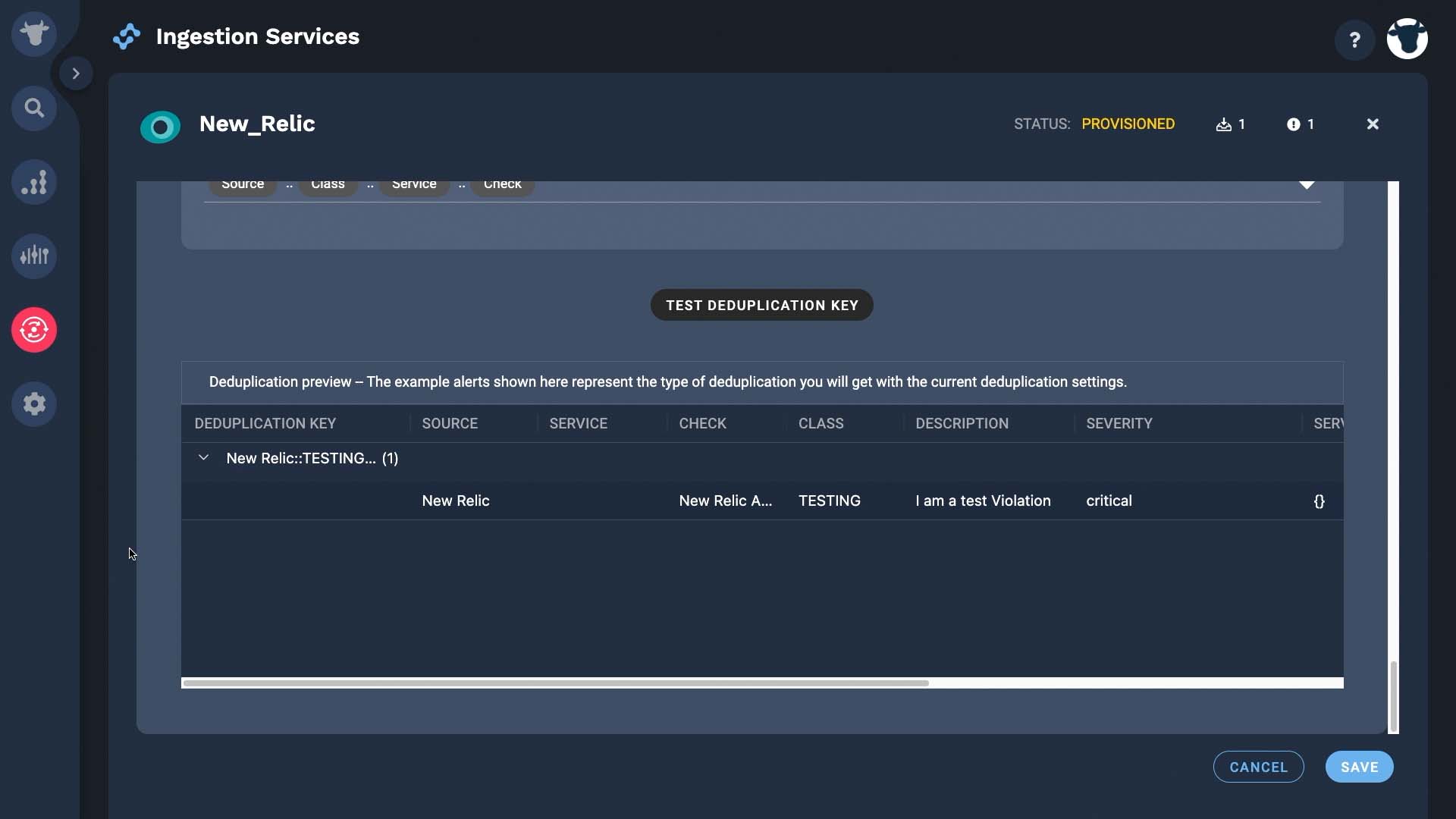
Our integration activates with data flowing in.
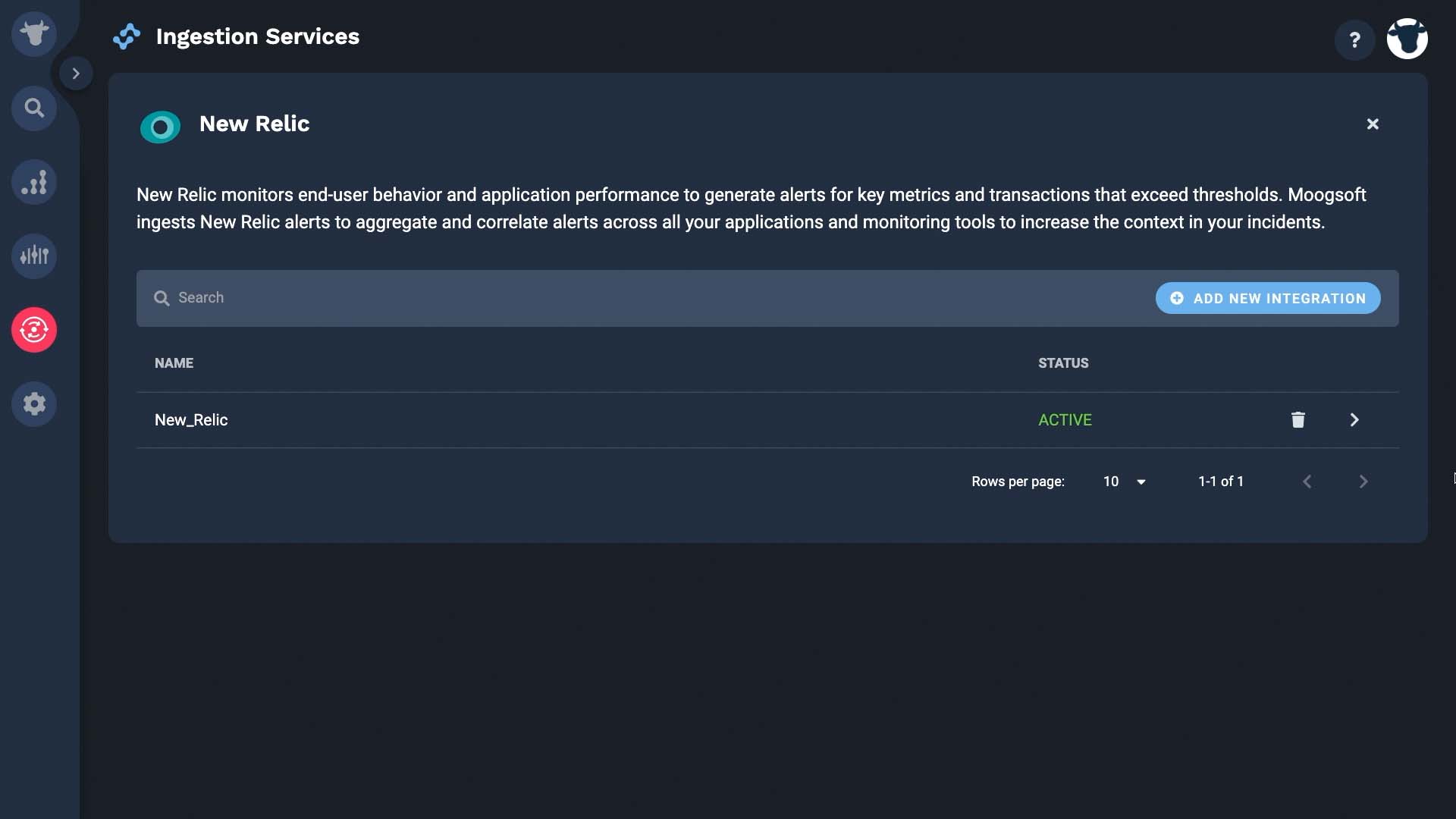
Now we can see our data from New Relic in the Alert view. Thanks for watching!