Concept Explainer: Correlation Engine best practices ►
This video explains how to get the most value out of the correlation engine by configuring scope filters, ranked definitions, and "catch-all" definitions.
In this video we’ll discuss tips and tricks to get the most value out of the correlation engine.
Correlation Engine groups related alerts into incidents, so your team can get the whole picture of an incident. In this video, you’ll learn the logic of alert correlation in detail.
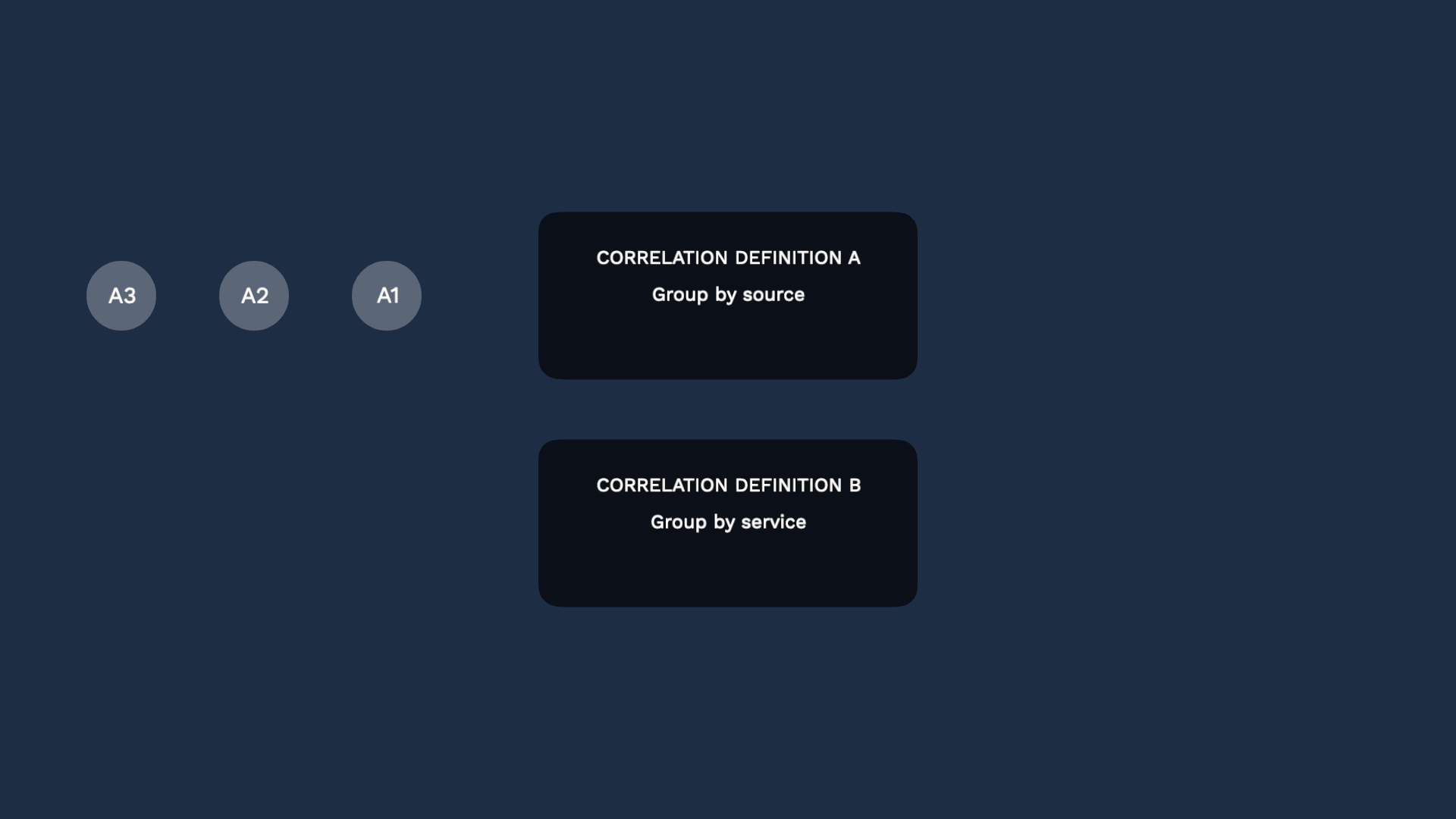
You start out with one default correlation definition which groups alerts from the same source.
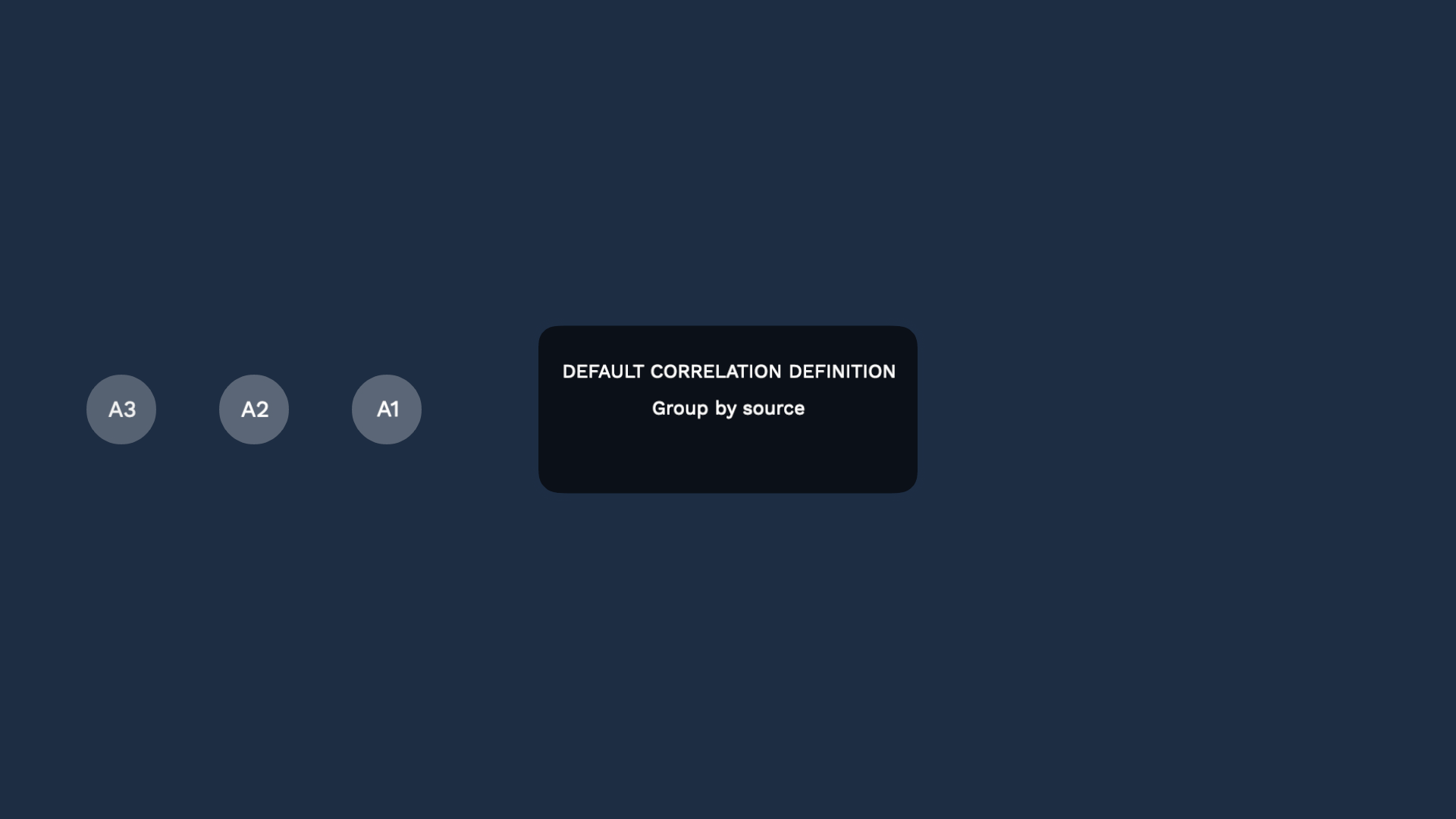
Every alert goes through this correlation definition, and is grouped into incidents.
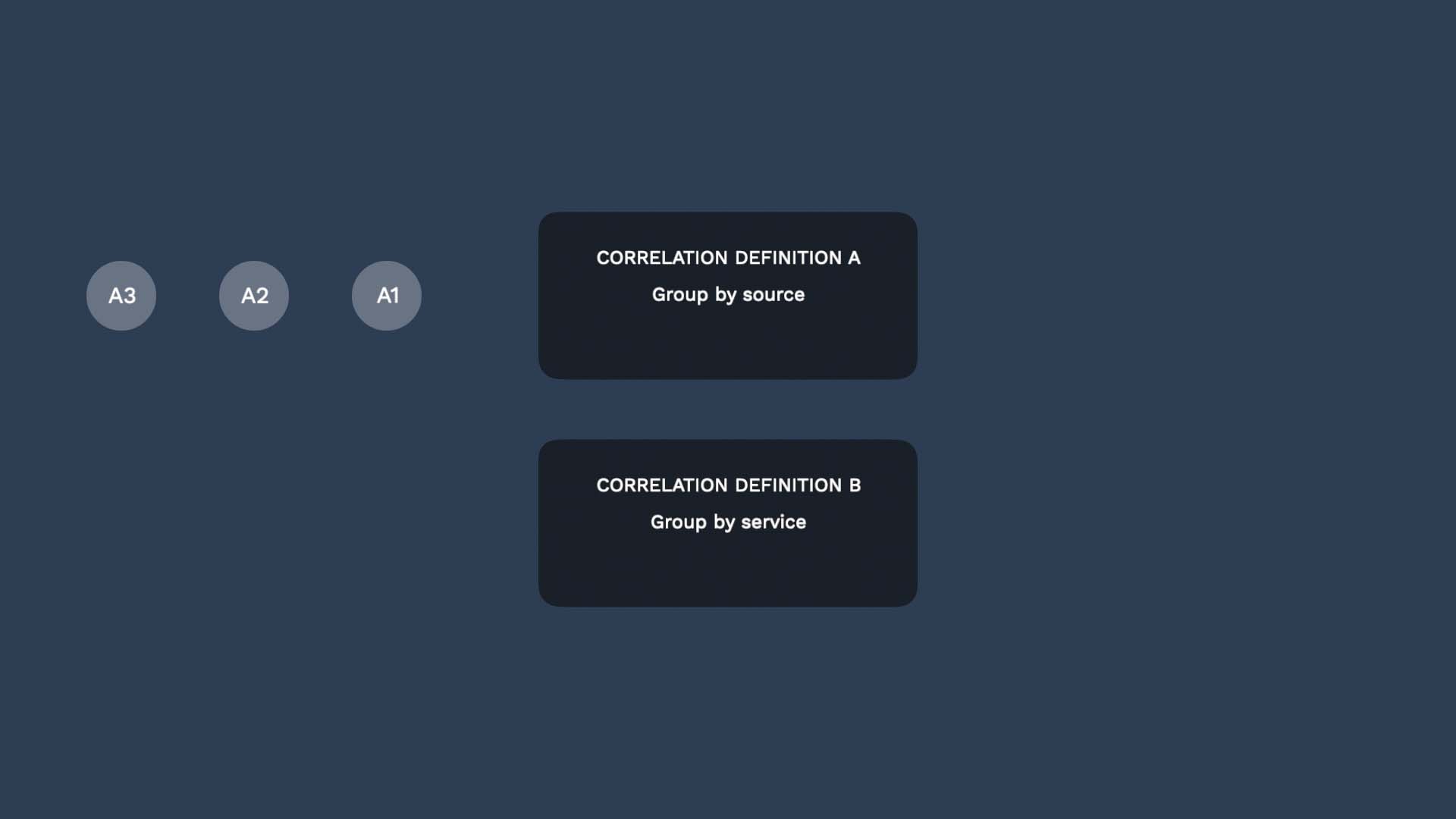
You can add any number of correlation definitions. Suppose you added a new definition to correlate alerts by impacted service.
By default, all alerts are evaluated by both definitions.Let’s say these alerts share the same source AND also impact the same service.
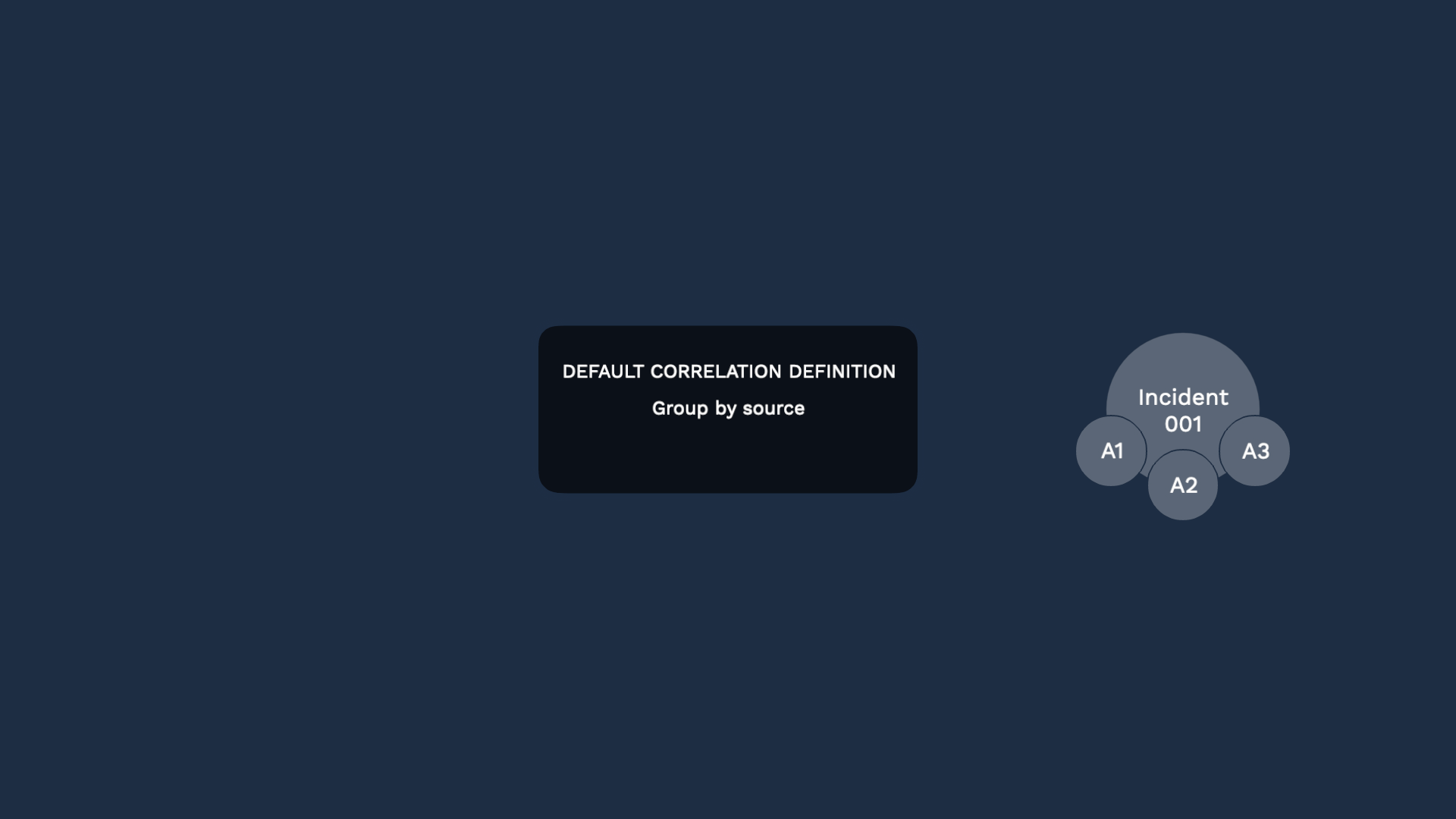
They hit the default correlation, and generate an incident. Then they also hit the new correlation definition.
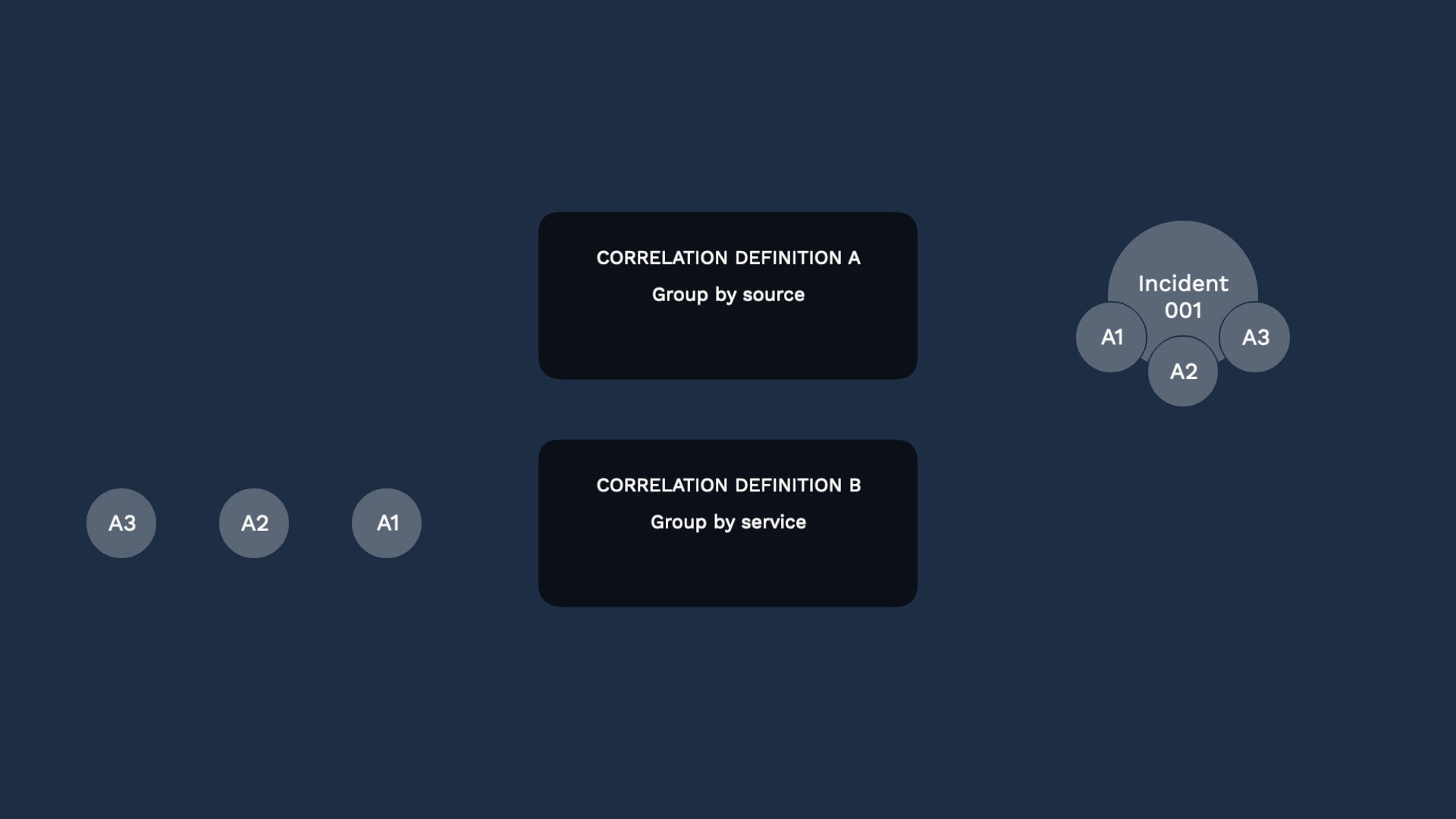
Correlation engine B recognizes they should be grouped. But Moogsoft recognizes there’s already incident 001, so it will not create another incident.
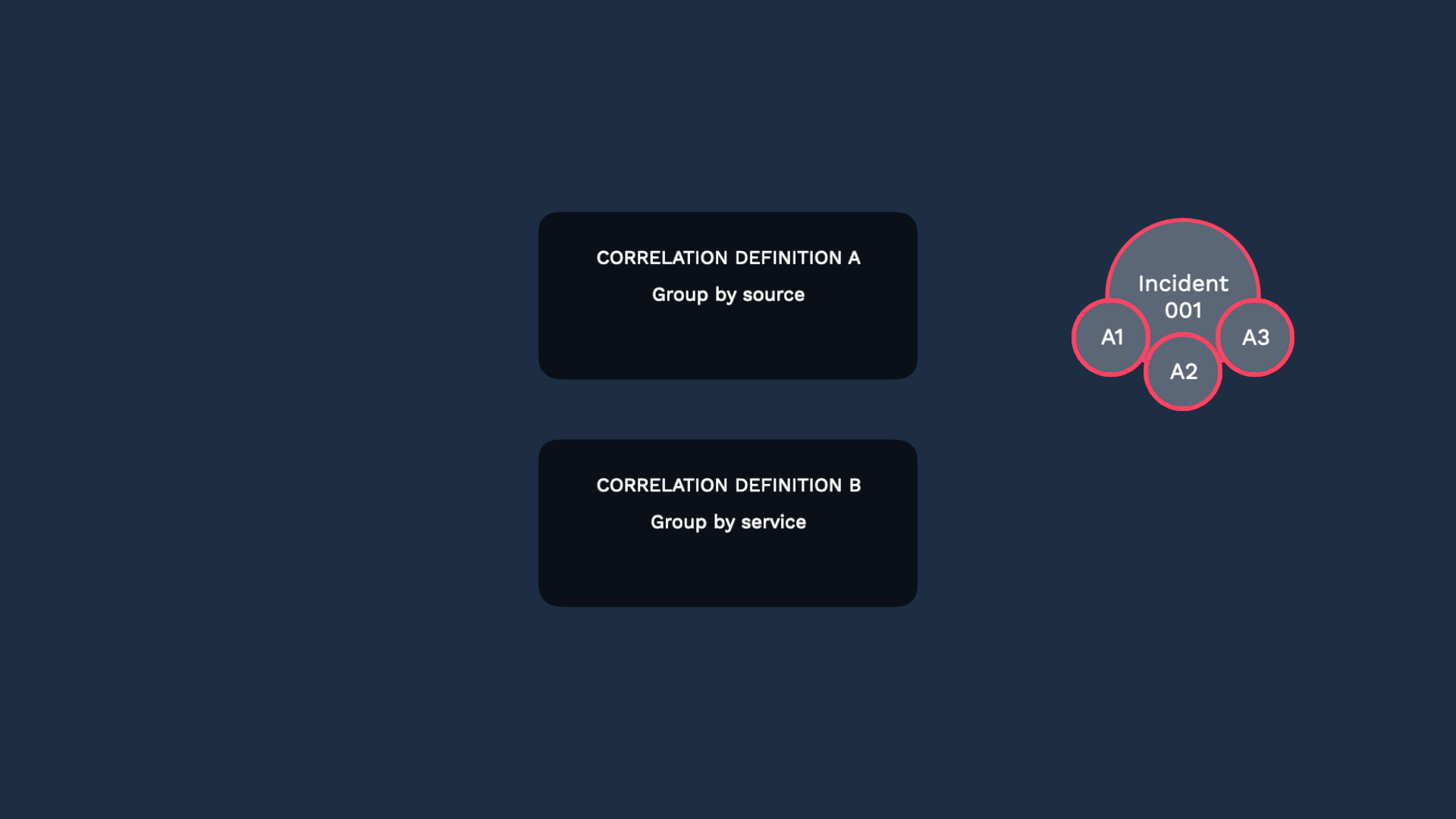
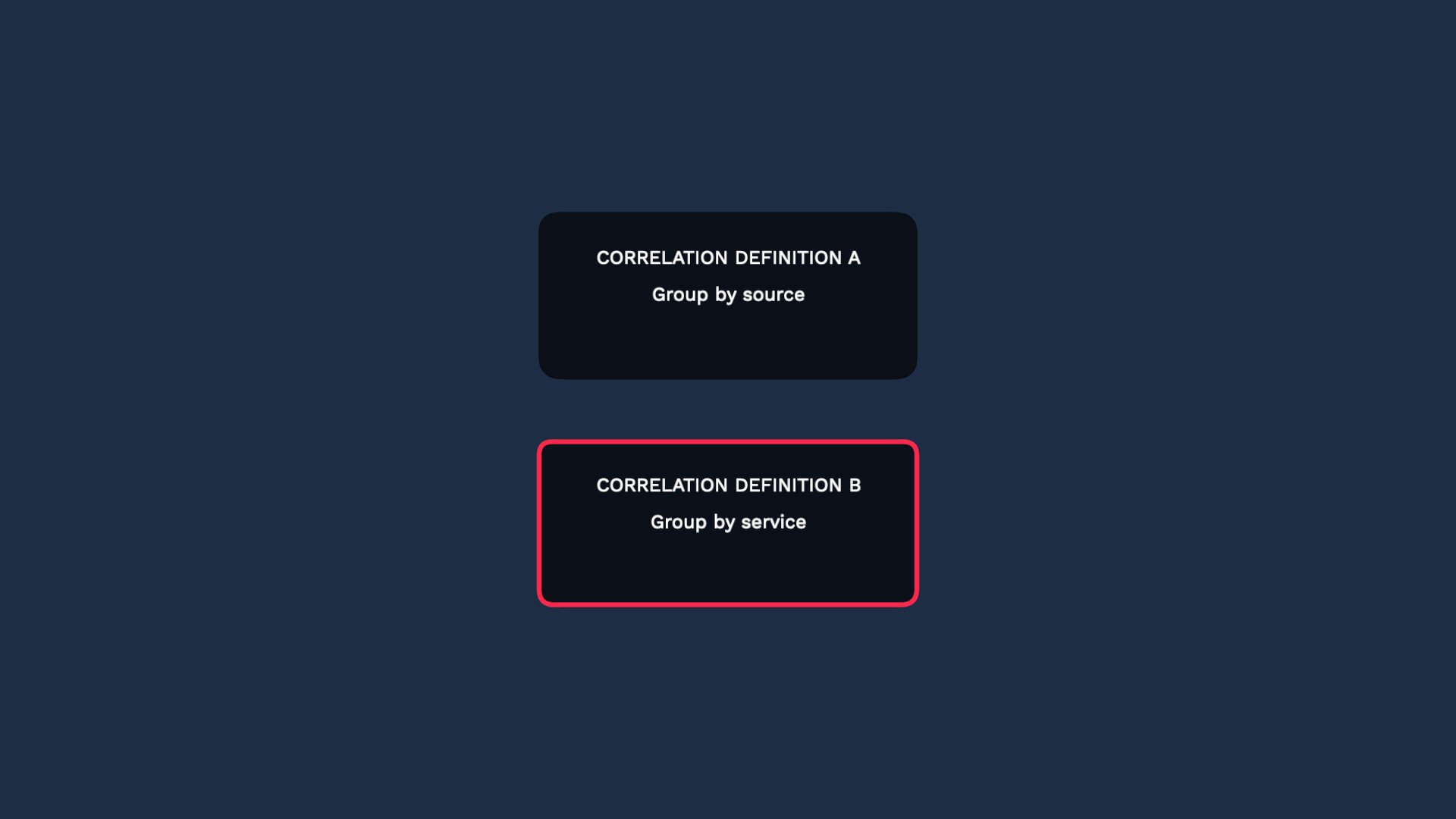
That’s smart! However, the best practice here is to add a scope filter, or use ranked definitions. Let’s look into each one.
A scope filter lets you define which alerts are eligible to be evaluated. So in this case, two of the alerts went through definition A, while others went through definition B.
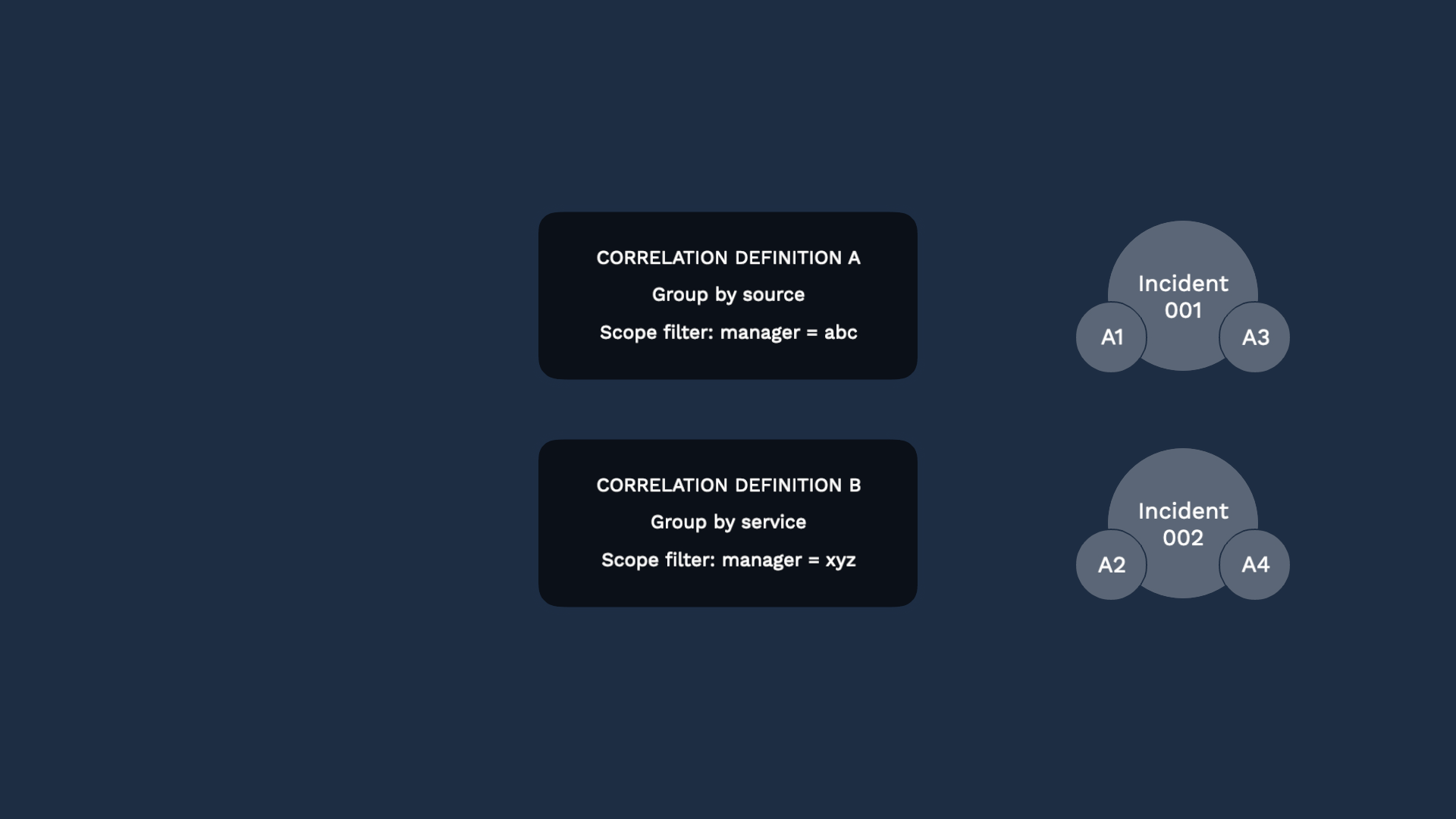
Some alerts may be evaluated by multiple correlation definitions and that’s totally fine. In this case, alert 002 appears in two different incidents and provides context and insights for both.
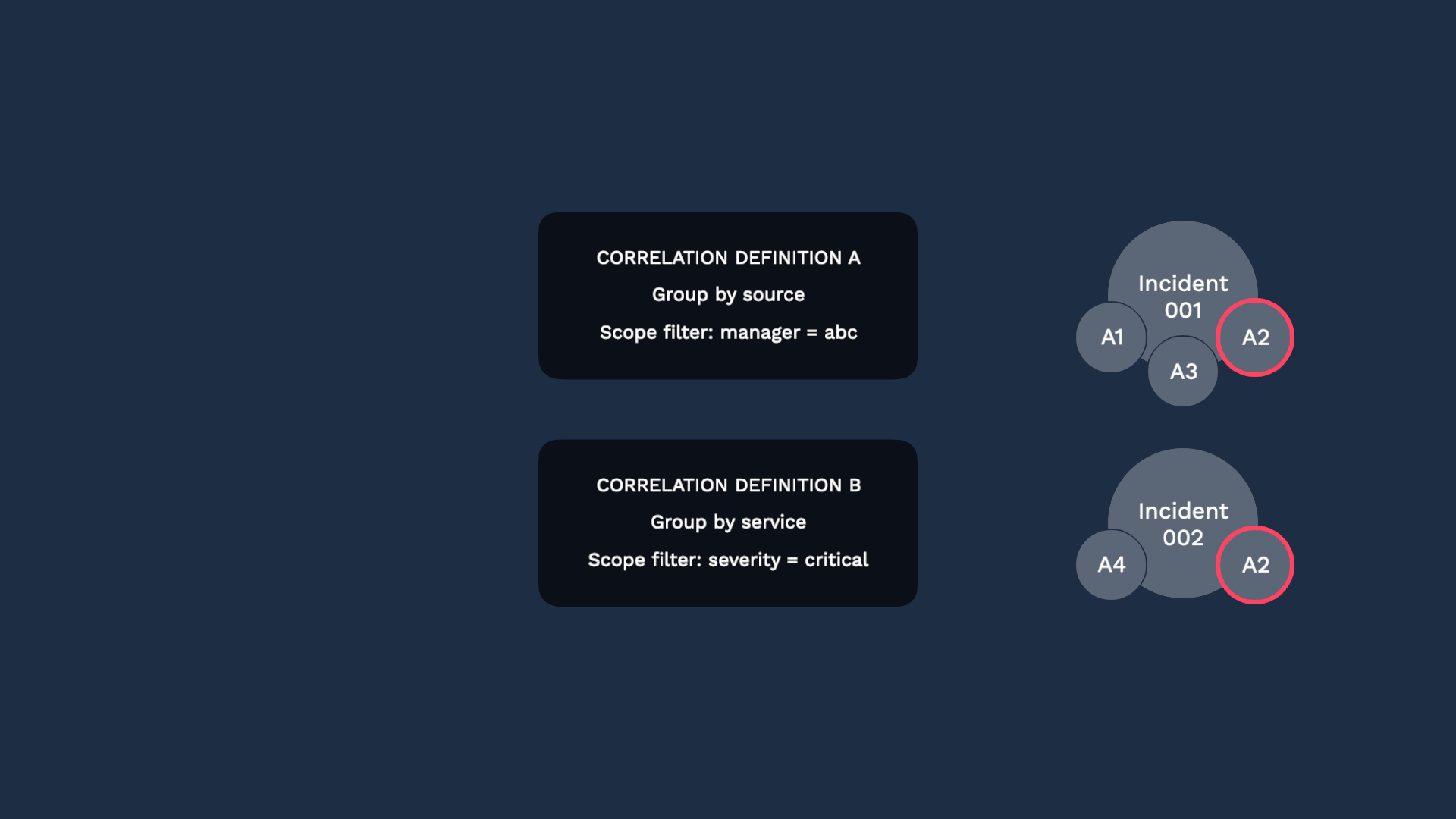
Another best practice is to use ranked definitions. You can rank your correlation definitions, so alerts are grouped by the first definition they match.
Let’s step through it. Here come 4 alerts. As they all hit definition A, Alert 001 and 003 match its correlation definition, so they form an incident.
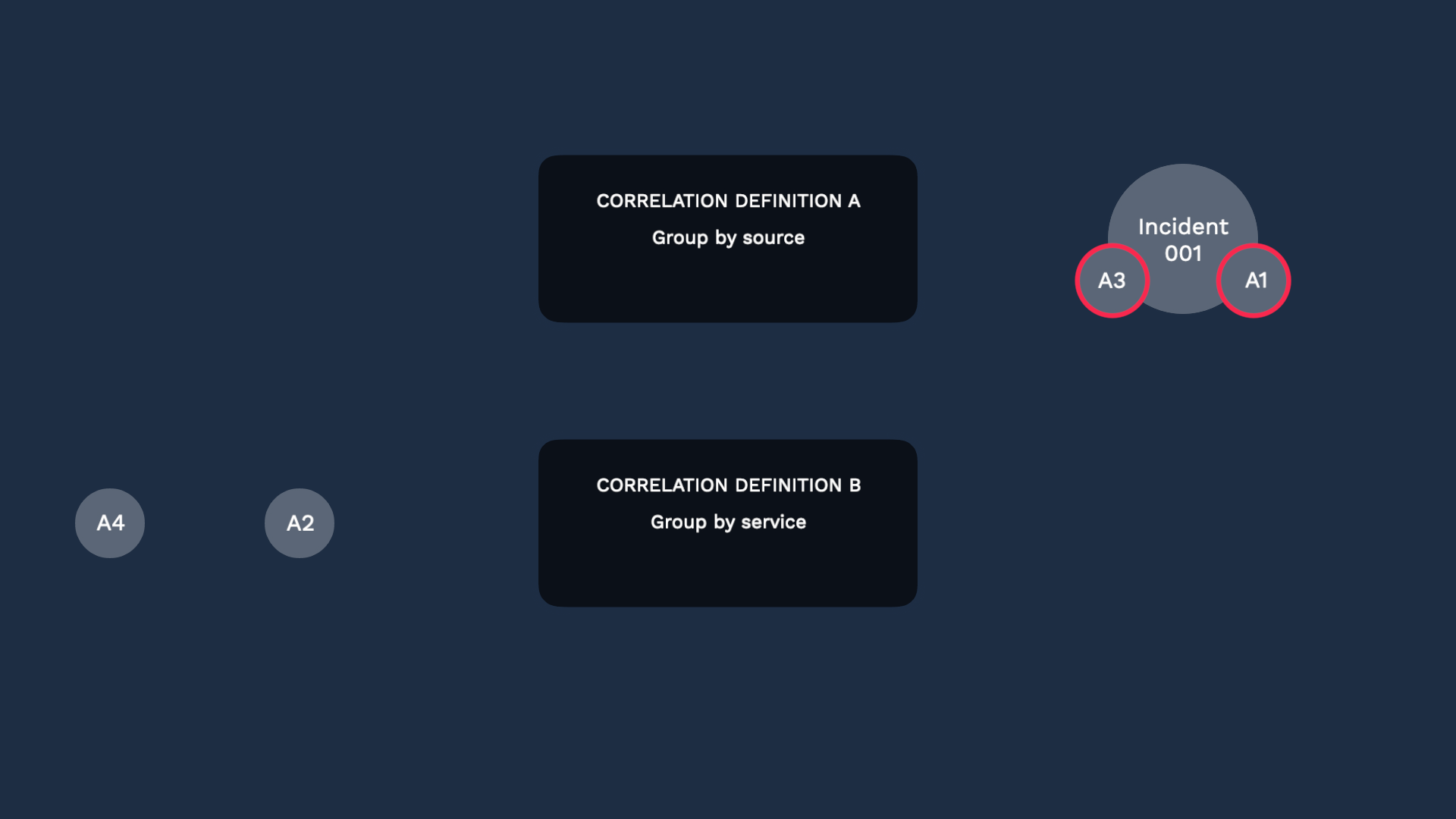
After that, these two alerts will not be evaluated further, so only these two will proceed to the next definition.
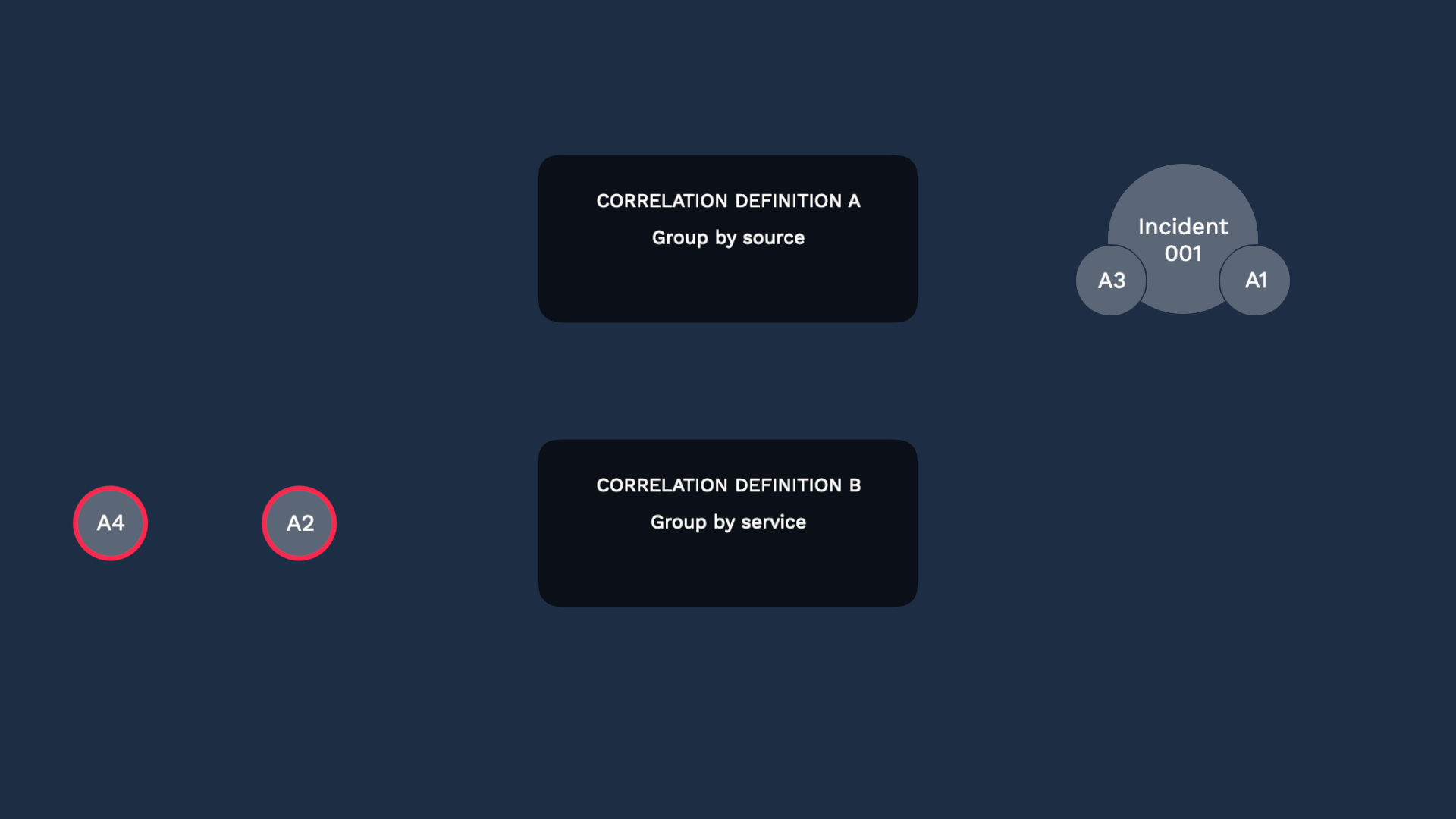
And let’s say they share the same impacted service, so they become another incident.
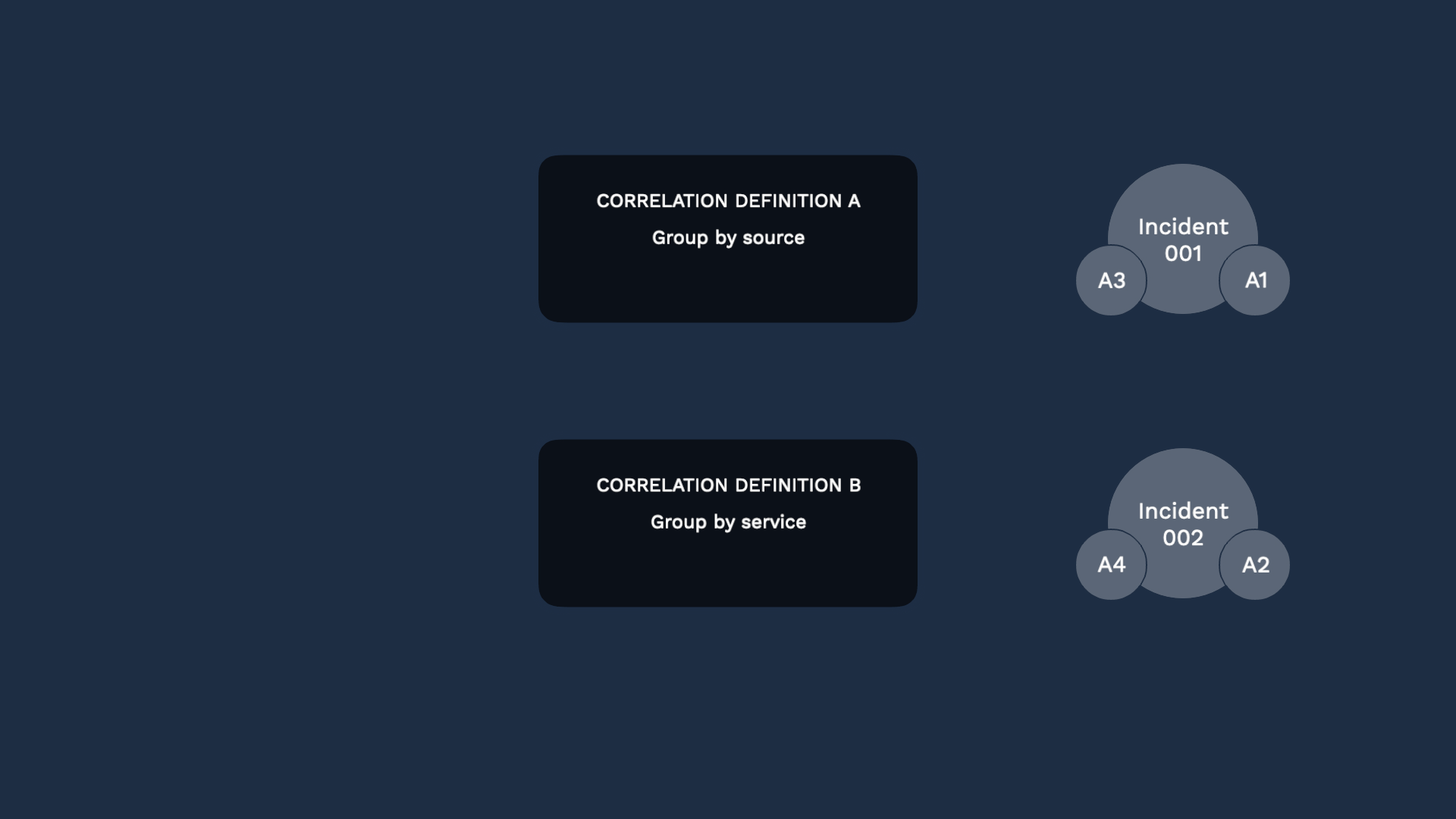
By ranking your correlation definition, you can control which definition your alerts should first be evaluated against.
Another best practice is to set up a “catch-all” definition.
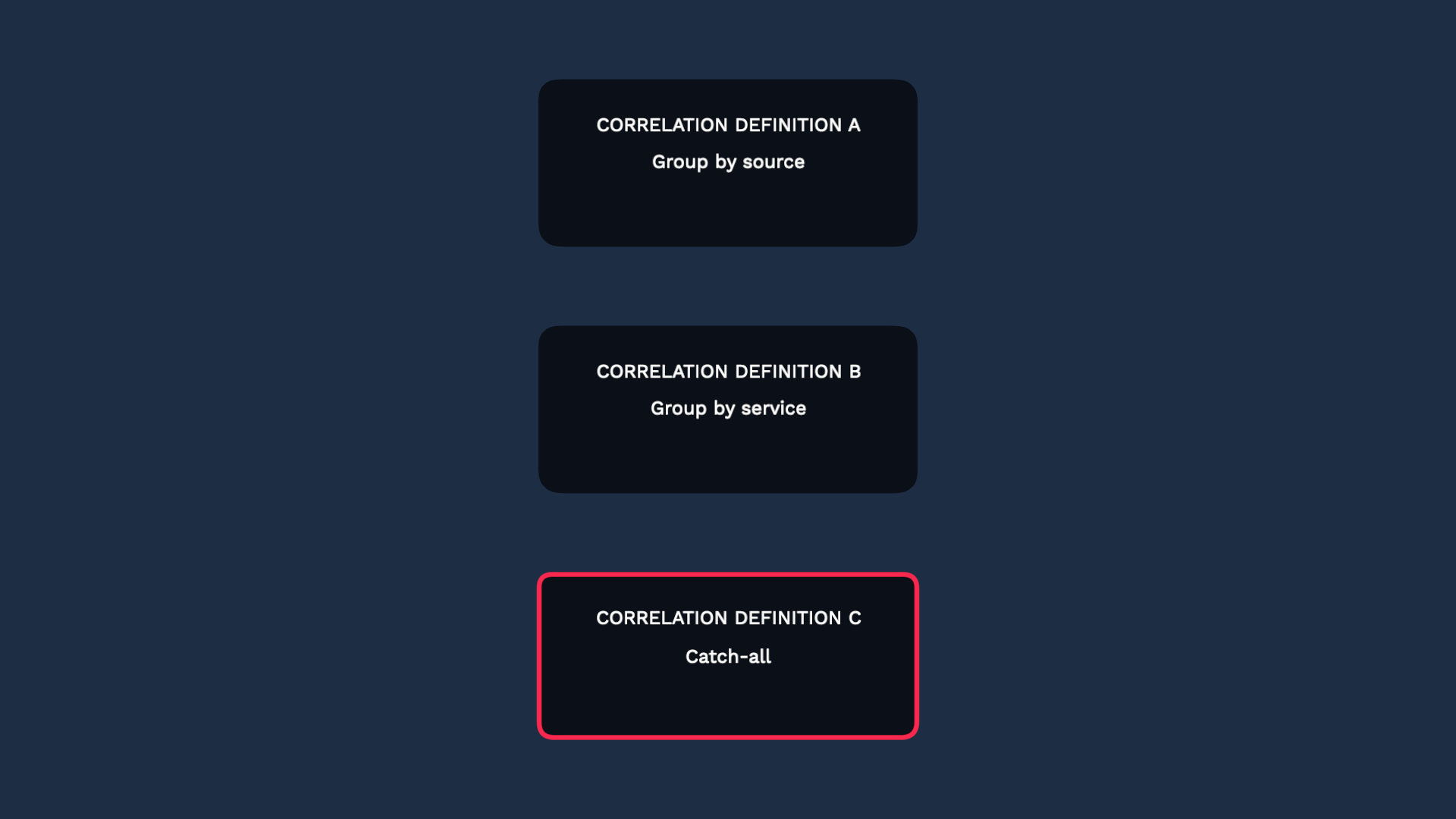
After your alerts go through your ranked correlation definitions, some alerts may remain un-grouped. If you want them to show up on the incidents page, set up a “catch-all” definition so each alert becomes an incident. That way those singleton alerts will not go unnoticed.
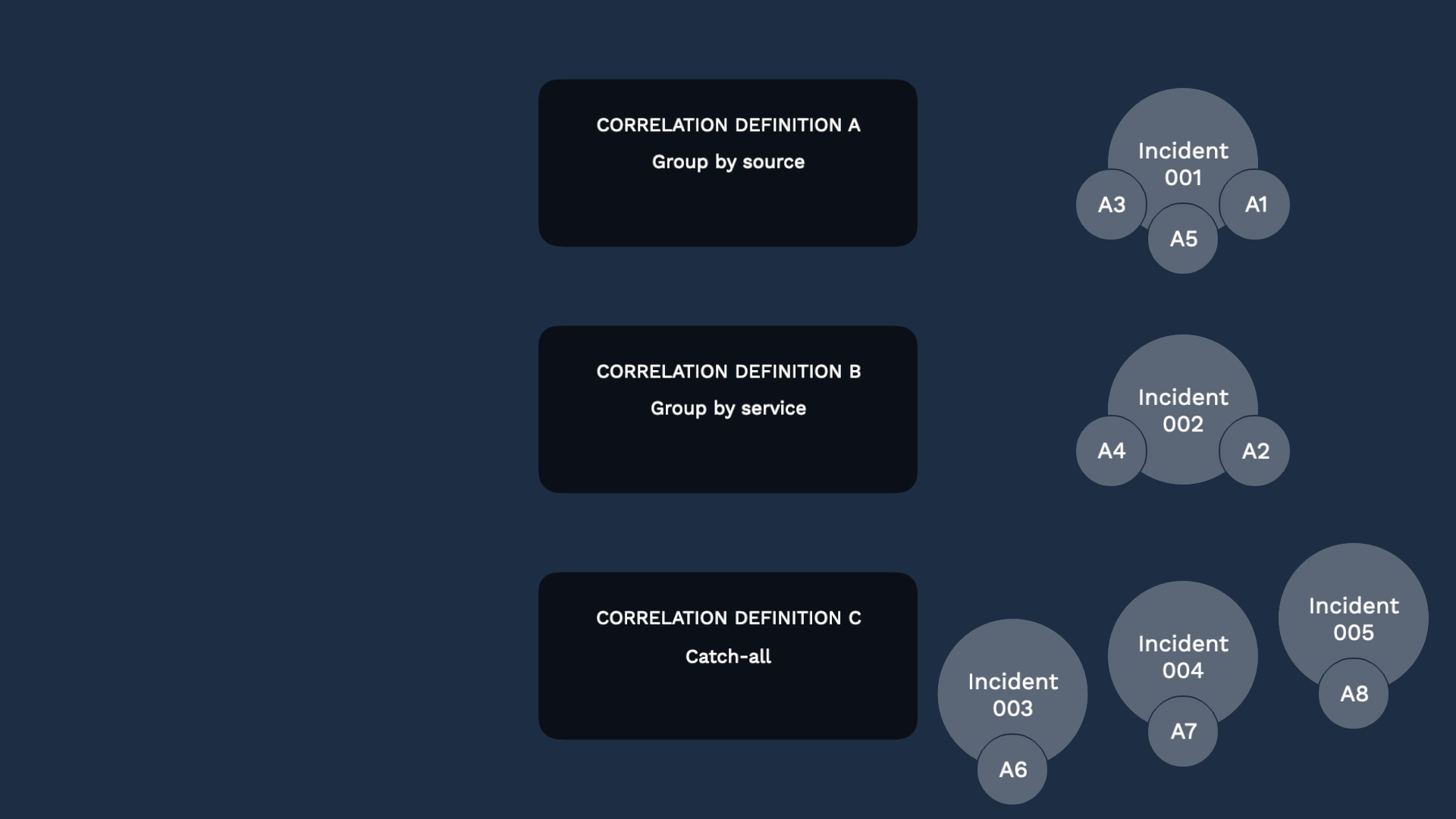
There is an easy toggle setting in the correlation engine to enable this.
Now you know how to get the most value out of the correlation engine. Thanks for watching!