Understand alerts and alert details
View the Moogsoft Cloud Alerts page by navigating to Incidents > Alerts.
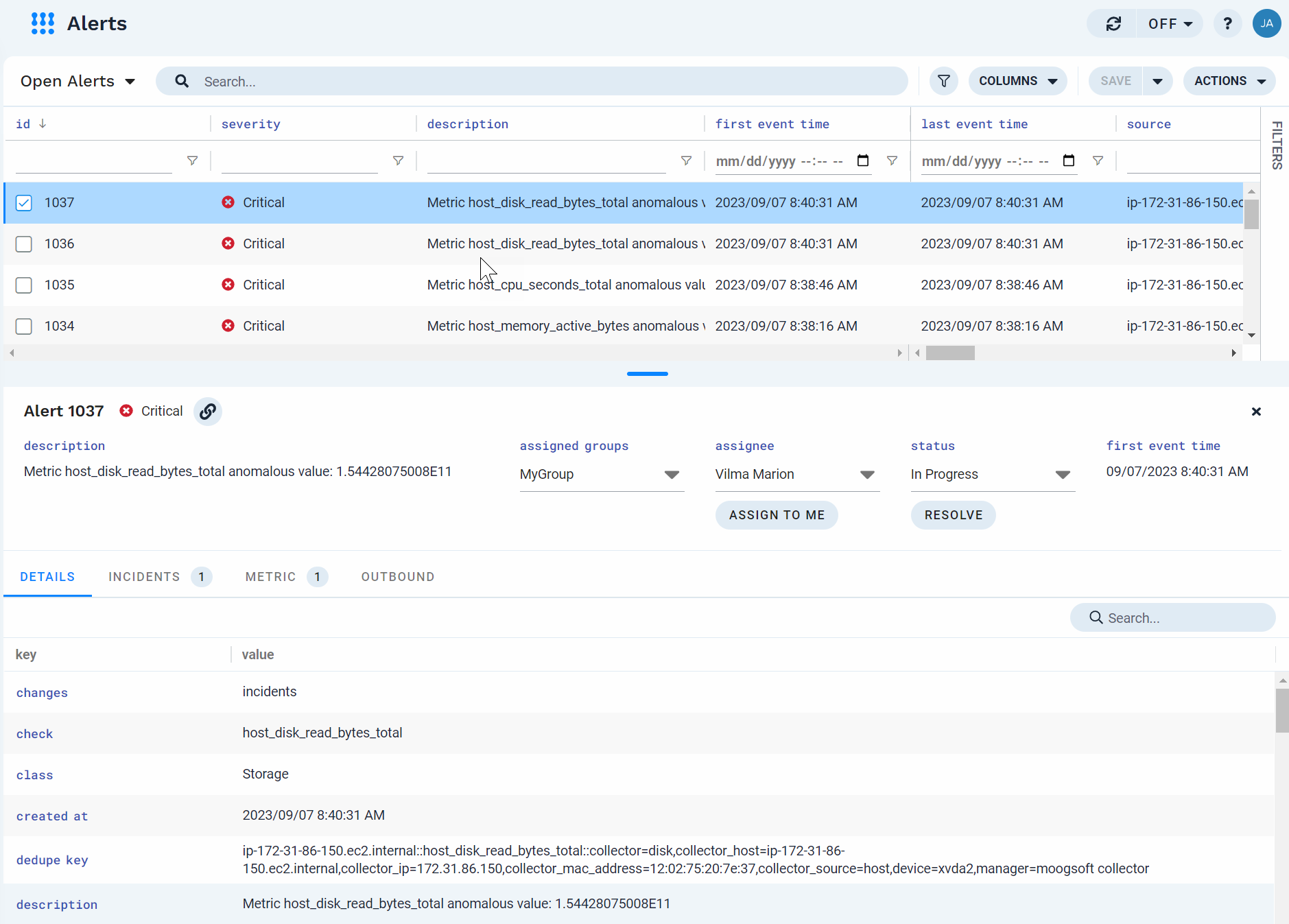
The Alerts page is divided into two panes: the top pane displays the total list of alerts in the current view, and the bottom pane displays details associated with the alert selected in the top pane. If multiple alerts are selected in the top pane, the details for the most recently select alert display in the bottom pane.
 |
Supported operations
You can do the following in this view:
Modify columns
Click Columns at the top of the page to access the following column options:
Add a column
In the Columns dialog, click Add Column and select a column to add to the view by clicking Add Column (+ icon) to the right of the column name. The column is added to the grid display.
If the column you want to add isn't in the list of recent columns, use the search box at the top of the dialog to locate it.
Pin (or unpin) a column
Pinning moves the column to the first position in the grid (or within the pinned group, if other columns are already pinned), "freezes" it in place, and allows the columns to the right of it to continue to scroll.
To pin a column, click the pin icon to the right of the column. This pins the column and all columns to the left of it.
If the column is already pinned, then clicking the pin icon unpins it.
Auto-size a column
To make a column as wide as the widest item in the column, click Auto-size this Column ( ↔ icon ) to the right of the column name.
Remove a column
Click Remove Column (trashcan icon) to the right of the column name.
Auto-size all columns
To change the width of all the columns to the width of the widest item in each column, click Auto-size All at the bottom of the dialog.
Update alerts
Update the assignee for the alert.
With an alert selected, click under assignee in the bottom pane and select a user from the list.
Update any groups assigned to the alert.
With an alert selected, click under assigned groups in the bottom pane and select one or more groups from the list.
Note
You can assign multiple groups to an alert, and you can unassign some or all of them.
Assigning a group to an alert does not assign the group to the the incident where the alert is a member.
Update the status of the alert (In Progress, Resolved, Closed).
With an alert selected, click under status in the bottom pane and select a status from the list.
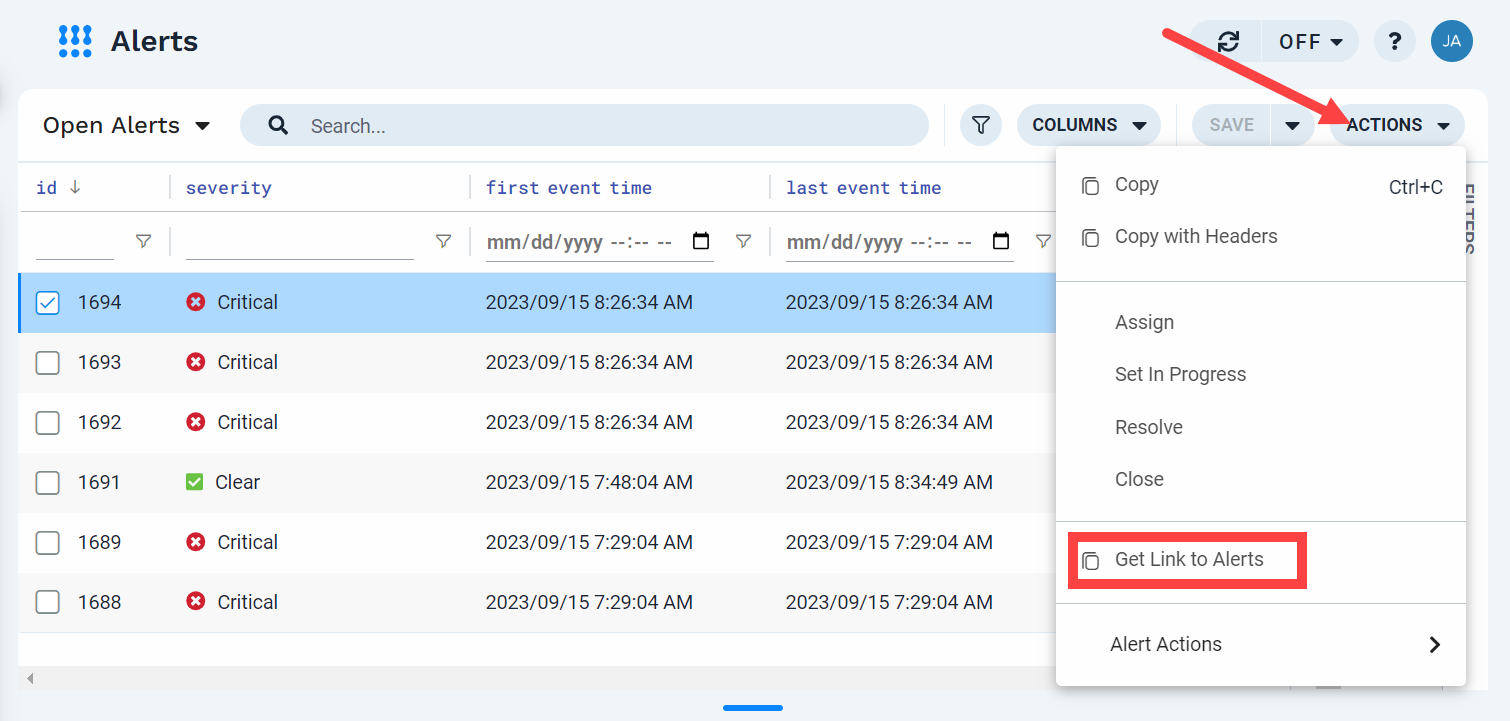
Use right-click alert actions
You can perform the following activities using the menu that displays when you right-click an alert in the pane.
What you can do | How to do it |
|---|---|
Copy an alert (with or without headers) | Right-click the alert and then click Copy on the menu. To include headers, click Copy with Headers. |
Assign an alert to a user | Right-click the alert and then click Assign on the menu. Select a user from the list that displays. |
Change the status of an alert to In Progress | Right-click the alert and then click Set in Progress on the menu. |
Resolve an alert | Right-click the alert and then click Resolve on the menu. |
Close an alert | Right-click the alert and then click Close on the menu. |
Create a maintenance window for this alert | Right-click the alert and then click Create maintenance window on the menu. The Maintenance Window feature opens with a new maintenance window configuration with the ID of the selected alert as the filter. If additional events are added to the selected alert during the maintenance window active time, then the alert information displays that it was affected by a maintenance window. |
Get a link to an alert that you can share with other users | Right-click the alert and then click Get Link to Alert on the menu. |
Use Action Menu alert actions with the alert | Right-click the alert and then click Alert Actions on the menu. Select the action you want to use. Note that you must first configure some alert actions before you can use them with alerts in the grid. |
Alert attributes
The following table describes the alert attributes which display in the Details tab.
Notes
Unless otherwise noted, the term "events" refers to both ingested event notifications and metric anomalies.
Moogsoft stores all timestamps in UTC format. The dates and times displayed in the UI are based on your browser's local time.
Column | Description |
|---|---|
alias | The alias for the alert source, as defined in the |
assigned groups | User groups assigned to this alert. |
assignee | User assigned to this alert. |
changes | The last change made to the alert. Multiple changes are possible, if they are made at the same time (as in a workflow, or when a new event changes multiple field values simultaneously). |
check | An identifier for the type of alert. For example, |
class | The high-level category of the performance issue reported by the alert. Examples include If a metric anomaly does not have a |
created at | The timestamp when Moogsoft ingested the first event, identified it as unique, and created the new alert. |
dedupe key | The unique identifier which describes this alert. Events with the same deduplication key belong to the same alert. |
description | The alert description, based on the |
event count | The number of events in the alert. |
external details | The number of sets of external details (objects in the array) in the alert. |
external details.external id | If the alert triggered an external notification based on an outbound webhook, this indicates the object (such as a ticket number) in the external system. |
external details.external link | HTML link to a system outside of Moogsoft. This is often, but not always, a link to the equivalent alert on the external system. |
external details.external name | The name of an outbound integration. |
external details.integration id | The outbound integration ID if the alert triggered an external notification based on an outbound webhook. |
external details.integration name | The outbound integration name if the alert triggered an external notification based on an outbound webhook. |
external details.integration type | Describes the type of integration. This information is determined by the outbound webhook configuration. |
external names | The names from the |
first event time | The timestamp of the first event or anomaly added to the alert. |
id | The alert ID. Moogsoft auto-generates the ID when it creates the alert. |
incidents | The list of incidents where this alert is a member. |
in maintenance | Displays |
last event time | The timestamp of the most recent event included in the alert. |
last status change time | The event time when the alert was last updated. |
location | You can include generic geolocation information in the |
maintenance | The ID of the last maintenance window that potentially impacted this alert. |
maintenance windows | A list of all maintenance windows potentially impacting this alert. |
manager | The generator or intermediary of the events in this alert. |
manager id | The unique identifier for the alert in the source system. |
namespace | An internal field used to set a metric identifier for any events which were generated via Anomaly Detection. |
originator | The system or service responsible for the last change to the alert. |
service | The external application or service that generated the ingested event or metric. This is a required field for ingested events and is used to identify duplicate and similar events. |
severity | Current severity of the alert, determined by the most recent event in the alert, in string format. |
severity high water | The highest severity an alert has reached. |
severity numeric | Current severity of the alert, determined by the most recent event in the alert, in numerical format. |
source | The node where the original events and/or anomalies occurred. This is typically an IP or fully qualified domain name. |
status | The alert status in string format. |
status numeric | The numeric alert status. |
tags | The optional tags included in this alert. You can specify tags during ingestion, or use event enrichment to add tags after ingestion. |
type | The type of the alert. The |